La suppression des logiciels malveillants WordPress est le processus de détection, nettoyage, et empêcher les codes malveillants qui compromettent l’intégrité de votre site Web. Les logiciels malveillants peuvent perturber considérablement les performances du site, conduire à des violations de données, endommager les classements SEO, et nuire aux visiteurs.
La suppression efficace des logiciels malveillants nécessite de comprendre le type d'infection, suivi des modifications dans les fichiers et les bases de données, et appliquer des méthodes de remédiation manuelles et automatisées, qui sont considérés ci-dessous.
Pourquoi la suppression des logiciels malveillants WordPress est importante?
Les sites Web WordPress sont particulièrement vulnérables en raison de leur popularité et de leur dépendance aux plugins et aux thèmes.. Les attaquants exploitent souvent des plugins obsolètes, références faibles, ou des serveurs non sécurisés pour injecter des scripts malveillants.
Pour les sites hébergés sur un VPS, la suppression des logiciels malveillants devient encore plus critique car les environnements VPS non gérés permettent aux pirates d'exploiter les vulnérabilités au niveau du serveur. En traitant correctement les menaces de logiciels malveillants, les propriétaires de sites Web garantissent la stabilité du site, sécuriser les données des utilisateurs, et maintenir la confiance des moteurs de recherche.
Selon Jus’s 2023 Rapport sur les menaces:
« WordPress reste le CMS le plus ciblé, comptabilité 92% de tous les sites Web infectés analysés. La principale cause de ces compromissions provient des vulnérabilités au sein de son écosystème, plugins et thèmes particulièrement obsolètes ».

Hébergement Web WordPress
À partir de 3,99 $ / mensuel

5 Infections malveillantes courantes à connaître
La reconnaissance des types d'infection ci-dessous garantit que la stratégie de suppression s'attaque à la cause première, pas seulement les symptômes visibles.
- Raies: Scripts cachés qui permettent aux pirates de retrouver l'accès même après avoir nettoyé le site. Ceux-ci résident souvent dans wp-config.php, fonctions.php, ou fichiers de plugin.
- Astuces pharmaceutiques: Contenu spam injecté, publicités généralement pharmaceutiques, qui apparaissent dans les résultats de recherche, SEO préjudiciable.
- Redirections malveillantes: Les visiteurs sont redirigés vers des sites Web dangereux, souvent causé par des fichiers .htaccess modifiés ou des injections JavaScript.
- Téléchargements au volant: Les logiciels malveillants se téléchargent automatiquement sur les appareils des visiteurs, présentant des risques de sécurité pour les utilisateurs.
- Scripts malveillants: Code JavaScript ou PHP injecté dans les fichiers du site pour voler des données ou manipuler le comportement du site Web.
Signes que votre site WordPress est infecté
L’identification précoce d’une infection peut éviter des dommages importants. Les utilisateurs VPS doivent surveiller les journaux du serveur, modifications de fichiers, et activités insolites. Les signes indiquent souvent si des logiciels malveillants sont actifs dans les fichiers principaux, plugins, ou des thèmes.
- Baisse soudaine du trafic: La mise sur liste noire par Google ou les fournisseurs d'hébergement peut réduire le trafic organique.
- Pop-ups ou publicités inhabituelles: Contenu inattendu sur vos pages, souvent lié à des logiciels malveillants.
- Utilisateurs inconnus: Comptes d'administrateur nouvellement créés sans votre autorisation.
- Fichiers modifiés ou supprimés: Modifications de fichiers qui n'ont pas été effectuées par le propriétaire du site.
- Performances lentes du site Web: Crashes inexpliqués du site ou utilisation intensive des ressources.
- Alertes de plugin de sécurité: Des plugins comme Wordfence ou iThemes Security détectent les activités suspectes.
Les outils de surveillance tels que ServerAvatar ou les panneaux de contrôle VPS peuvent fournir des analyses en temps réel sur les ressources du serveur et l'intégrité des fichiers pour détecter rapidement les infections..

Que faire avant de supprimer les logiciels malveillants sur WordPress
Avant de lancer la suppression des logiciels malveillants, la préparation est essentielle pour éviter que l’attaque ne se propage ou ne provoque des dommages irréversibles. Ignorer ces étapes peut entraîner des infections persistantes ou une perte de données.

Serveur VPS pas cher
À partir de 2,99 $/mois
- Restreindre l'accès à WordPress: Limitez l'accès au site via .htaccess pour empêcher les visiteurs de déclencher des logiciels malveillants ou des redirections de phishing. Autorisez votre adresse IP uniquement pendant le nettoyage.
- Sauvegarder les fichiers WordPress: Les sauvegardes complètes des fichiers et des bases de données vous permettent de comparer les données infectées et les données propres., s'assurer qu'aucun fichier critique n'est perdu lors de la suppression.
- Vérifier les modifications récentes: Examiner les journaux et les fichiers récemment modifiés pour identifier la source du logiciel malveillant. Des commandes comme « trouver . -tapez f -ctime -3 » peut localiser les fichiers récemment modifiés.
- Mettre à jour les mots de passe et les clés d'accès: Changez immédiatement tous les administrateurs, base de données, et mots de passe FTP pour empêcher les pirates de maintenir l'accès.
- Supprimer les liens symboliques: Supprimer les liens symboliques qui pourraient être exploités pour l'accès aux fichiers.
- Mettre à jour WordPress, Plugins, Thèmes, et PHP: Assurez-vous que le CMS et les extensions sont corrigés pour corriger les vulnérabilités.
- Réinitialiser les autorisations de fichiers et de dossiers: Définir des autorisations pour sécuriser les fichiers et répertoires sensibles, typiquement 644 pour les fichiers et 755 pour les dossiers.
- Analysez votre ordinateur à la recherche de logiciels malveillants: Empêchez la réinfection en vous assurant que votre appareil local est propre avant de vous reconnecter au VPS.
Comment supprimer manuellement les logiciels malveillants de votre site WordPress
Pour les utilisateurs ayant des connaissances techniques, la suppression manuelle des logiciels malveillants offre le nettoyage le plus approfondi et vous donne un contrôle total sur votre site’l'intégrité. Alors que les outils automatisés offrent une solution rapide, ils peuvent parfois passer à côté de menaces profondément ancrées.
Voyons donc les étapes et commandes exactes nécessaires pour rechercher et détruire le code malveillant., nettoyer votre base de données, et sécurisez votre site internet:
Étape 1: Isolez votre site et créez une sauvegarde complète
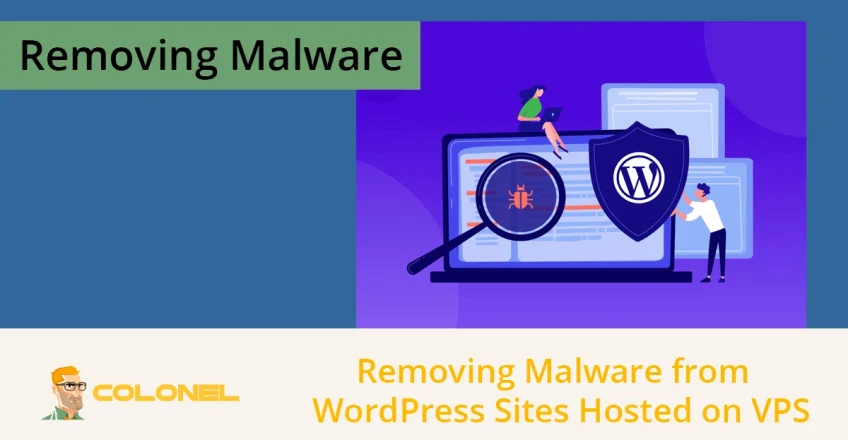
D'abord, mettez votre site hors ligne pour empêcher la propagation des logiciels malveillants et protéger vos visiteurs. Vous pouvez utiliser un plugin de maintenance ou, pour un meilleur contrôle, ajoutez le code suivant à votre fichier .htaccess. Cela bloque tous les visiteurs sauf vous.
(N'oubliez pas de remplacer YOUR.IP.ADDRESS par votre adresse IP actuelle)
htaccess
<IfModule mod_rewrite.c>

Hébergement VPS Windows
Remote Access & Full Admin
Réécrire le moteur activé
# Autorisez votre IP à accéder au site
RéécritureCond %{REMOTE_ADDR} !^VOTRE.IP.ADRESSE$
# Rediriger tout le reste du trafic
RéécritureCond %{REQUEST_URI} !^/maintenance.html$
Réécrire la règle .* /maintenance.html [R=503,L]
</SiModule>
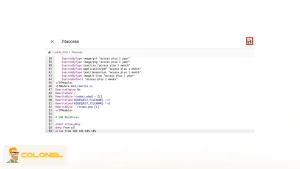
Suivant, créez une sauvegarde complète de vos fichiers et de votre base de données. Ceci est votre filet de sécurité. Connectez-vous à votre serveur via SSH et exécutez ces commandes:
frapper
# Sauvegarder les fichiers du site Web
tar -czvf site_backup_files.tar.gz /path/to/your/public_html
# Sauvegarder la base de données
Mysqldump -u nom_base de données -p mot de passe base de données > base de données_backup.sql
Étape 2: Réinstaller et comparer les fichiers de base de WordPress
Les fichiers principaux infectés sont un problème courant. Commencez par réinstaller une nouvelle version de WordPress. Si vous avez accès au tableau de bord, allez dans Tableau de bord → Mises à jour et cliquez sur Réinstaller maintenant.
Sinon, utilisez WP-CLI via SSH pour une installation propre, qui écrasera les dossiers principaux wp-admin et wp-includes:
frapper
# Téléchargez les derniers fichiers de base de WordPress, ignorer le répertoire wp-content
wp téléchargement de base –ignorer le contenu –forcer
Maintenant, vérifier l'intégrité de votre installation. Cette commande WP-CLI compare vos fichiers aux sommes de contrôle officielles de WordPress pour rechercher des modifications.:
frapper
# Rechercher les fichiers principaux modifiés
wp core checksums de vérification
Tout fichier qui renvoie un « La somme de contrôle ne correspond pas » l'erreur est suspecte et nécessite une enquête.
Étape 3: Recherchez les portes dérobées cachées dans vos fichiers
Les pirates adorent cacher des portes dérobées dans vos fichiers pour y accéder plus tard. Ceux-ci sont souvent obscurcis à l'aide de fonctions PHP comme base64_decode, exécutif, évaluer, et str_rot13.
Exécutez cette commande puissante via SSH pour rechercher dans tout votre répertoire les fichiers contenant ces fonctions suspectes:
frapper
trouver . -tapez f -nom ‘\*.php’ | xargs egrep -i « (mail|fsockopen|pfsockopen|stream_socket_client|exécutif|système|relais|évaluer|base64_decode) »
Soyez attentif aux résultats. Bien que certains plugins puissent utiliser ces fonctions légitimement, toute apparition dans des fichiers comme wp-config.php, fonctions.php, ou dans le dossier wp-content/uploads se trouve un signal d'alarme majeur.
Étape 4: Analyser la base de données à la recherche d'injections malveillantes
Les logiciels malveillants sont’pas seulement dans tes fichiers; il peut également être injecté directement dans votre base de données. Utilisez WP-CLI pour rechercher des modèles malveillants courants tels que <scénario> des balises ou des fonctions comme eval() et atob():
frapper
# Rechercher dans toute la base de données l'ouverture « <scénario » étiqueter
recherche dans la base de données wp « <scénario »
# Utilisez l'expression régulière pour rechercher plusieurs modèles suspects à la fois
recherche dans la base de données wp ‘(<scénario|évaluer(|CACHOT|deCharCode)’ –expression régulière
Notez tous les messages, pages, ou des options qui contiennent ces scripts. Vous les nettoyerez dans la phase suivante.

Étape 5: Nettoyer le répertoire wp-content/uploads
Le dossier de téléchargement ne doit contenir que des fichiers multimédias, pas de scripts PHP. Les pirates cachent souvent des portes dérobées ici. Exécutez cette commande pour rechercher tous les fichiers PHP dans ce répertoire:
frapper
trouver ./wp-content/uploads -type f -name « *.php »
Examinez attentivement tous les fichiers trouvés et supprimez-les.

Étape 6: Supprimer le code malveillant et nettoyer les fichiers
Revenez à la liste des fichiers infectés que vous avez trouvés à l'étape 3. Ouvrez chaque fichier et supprimez soigneusement le code malveillant que vous avez identifié. Ne supprimez pas l'intégralité des fichiers de thème ou de plugin, car cela casserait votre site. Plutôt, supprimer uniquement les éléments ajoutés, code obscurci. Si tu’je ne sais pas à quoi ressemblait le code d'origine, comparez-le à une nouvelle copie du thème ou du plugin.
Étape 7: Vérifier et nettoyer les comptes d'utilisateurs
Une tactique courante des pirates consiste à créer un utilisateur administrateur caché.. Dans votre tableau de bord WordPress, allez dans Utilisateurs → Tous les utilisateurs. Supprimez tous les comptes d'utilisateurs que vous n'avez pas’je ne reconnais pas.
Vous pouvez également utiliser WP-CLI pour obtenir une liste claire de tous les utilisateurs et de leurs rôles:
frapper
# Répertoriez tous les utilisateurs avec leur rôle et leur date de création
liste des utilisateurs wp –champs=ID,connexion_utilisateur,rôle,utilisateur_enregistré –orderby=user_registered
Rétrograder tous les utilisateurs qui ont un rôle plus élevé qu'ils ne le devraient (Par exemple, un « Abonné » qui est maintenant un « Administrateur »).
Étape 8: Réinitialiser tous les mots de passe et clés de sécurité
Supposons que toutes les informations d'identification ont été compromises. Tout réinitialiser:
- Tous les mots de passe des utilisateurs WordPress (surtout les administrateurs).
- Mot de passe de votre base de données.
- Mots de passe FTP et SSH.
- Mot de passe de votre compte d'hébergement.
Enfin, générer de nouvelles clés de sécurité WordPress (sels) et ajoutez-les à votre fichier wp-config.php. Vous pouvez obtenir de nouvelles clés auprès du générateur de sel officiel WordPress.
Étape 9: Demander un avis à Google
Si votre site a été signalé comme étant malveillant, vous devez demander à Google de l'examiner.
- Accédez à votre compte Google Search Console.
- Accédez à l'onglet Problèmes de sécurité.
- Confirmez que vous avez résolu les problèmes et cliquez sur « Demandez un examen. »
Ce processus peut prendre quelques jours, mais ça’est essentiel pour supprimer tout avertissement des résultats de recherche et restaurer la réputation de votre site.
Comment supprimer automatiquement les logiciels malveillants WordPress
Si votre site WordPress est compromis, vous pouvez supprimer l'infection rapidement sans étapes manuelles complexes. Les deux méthodes automatisées les plus simples sont:
Utilisez un plugin WordPress Malware Scanner
La solution de bricolage la plus simple consiste à utiliser un plugin de sécurité. Des outils comme WordFence agissent comme un antivirus pour votre site Web, vous permettant d'analyser l'intégralité de votre site et de supprimer le code malveillant en quelques clics. Voici comment ça marche:
- Installer et numériser: Si vous pouvez accéder à votre tableau de bord d'administration WordPress, installez un plugin de sécurité comme Wordfence. Accédez à sa fonction d'analyse et exécutez une analyse complète du site.
- Identifier les menaces: Le plugin vérifiera vos fichiers principaux, thèmes, plugins, et base de données, puis fournissez une liste de tous les logiciels malveillants identifiés, portes dérobées, et code suspect.
- Nettoyer automatiquement: À côté de chaque menace identifiée, vous verrez des options comme « Supprimer le fichier » ou « Réparation. » Cliquez simplement sur l'action recommandée, et le plugin se chargera du nettoyage pour vous.
La limite: Cette méthode ne fonctionne que si vous avez accès à votre tableau de bord d'administration WordPress. Les cyberattaquants vous excluent souvent, ce qui rend impossible l'installation et l'utilisation d'un plugin. Si tu’je suis en lock-out, passer à la méthode suivante.
Utilisez votre hôte’s Scanner de logiciels malveillants intégré
Si vous le pouvez’ne pas accéder à votre tableau de bord d'administration, votre hébergeur est votre prochain meilleur ami. De nombreux hébergeurs WordPress gérés fournissent des outils de sécurité intégrés auxquels vous pouvez accéder directement depuis votre Hébergement WordPress Panneau de contrôle:
- Connectez-vous à votre panneau d'hébergement: Accédez à votre compte d'hébergement’le panneau de commande (comme hPanel, cPanel).
- Accédez à la section Sécurité: Recherchez un élément de menu comme « Sécurité » ou « Scanner de logiciels malveillants. »
- Exécutez l'analyse: Cet outil analysera automatiquement tous les fichiers de votre site Web au niveau du serveur et supprimera tous les logiciels malveillants détectés.. Vous ne’je n'ai pas besoin de faire quoi que ce soit manuellement. Vous verrez un rapport confirmant que votre site est propre ou détaillant le malware qui a été supprimé..
C'est la solution parfaite lorsque vous’je suis exclu de WordPress, car l'analyse s'exécute indépendamment de votre site Web’le tableau de bord.
Conclusion
Nettoyer les logiciels malveillants d'un site WordPress hébergé sur un VPS implique bien plus que la suppression des fichiers suspects. Cela nécessite une action coordonnée tout au long du confinement, balayage, correction manuelle, restauration de fichiers et de bases de données, rotation des titres de compétences, et durcissement complet. Étant donné que les logiciels malveillants peuvent résider dans les fichiers principaux, thèmes, plugins, télécharge des dossiers, et tables de base de données, seule une approche à plusieurs niveaux et globale permet un rétablissement complet.
Après le nettoyage, mettre en œuvre des mesures de durcissement fortes telles qu’un WAF, authentification à deux facteurs, autorisations contrôlées, et l'analyse de routine améliore considérablement la résilience à long terme. La suppression efficace des logiciels malveillants WordPress combinée à une maintenance disciplinée garantit une sécurité durable pour l'environnement VPS..
Questions fréquemment posées (FAQ)
Comment savoir si mon site WordPress est infecté par un malware?
Les indicateurs courants incluent les redirections non autorisées, comptes d'administrateur inconnus, fichiers modifiés, utilisation inhabituelle des ressources du serveur, Spam SEO, et modifications inattendues des articles ou des pages.
Quel est le moyen le plus rapide de supprimer les logiciels malveillants de WordPress?
L'option la plus rapide consiste à utiliser un scanner de sécurité automatisé comme Wordfence ou Sucuri., qui identifie les fichiers malveillants et les supprime avec un minimum d'effort manuel.
Les logiciels malveillants peuvent-ils réapparaître après la suppression?
Oui. La réinfection se produit lorsque la vulnérabilité d'origine n'est pas corrigée. Vous devez mettre à jour WordPress, plugins, thèmes, mots de passe, et configurations de serveur.
Un VPS augmente-t-il la sécurité de WordPress?
Un VPS offre une meilleure isolation, Ressources dédiées, et un contrôle plus profond par rapport à l'hébergement partagé, mais cela nécessite une configuration appropriée.
Dois-je réinstaller WordPress après le nettoyage des logiciels malveillants?
La réinstallation des fichiers principaux est recommandée car elle garantit que tous les composants essentiels sont propres. Cette étape ne supprime pas votre contenu et garantit l'intégrité du code.
