
Composants du serveur React (RSC) ont considérablement amélioré les performances des applications Web en permettant le traitement côté serveur tout en maintenant la réactivité de React côté client. Cependant, une faille de sécurité critique, nommé React2Shell (CVE-2025-55182), a été découvert qui menace des millions d'applications Web. Cette vulnérabilité permet l'exécution de code à distance non authentifié (RCE) et porte un indice de gravité maximal de CVSS 10, soulignant son caractère critique.
Dans ce guide, nous explorons les détails de React2Shell, cadres concernés, risques potentiels, étapes d'atténuation, et les meilleures pratiques pour sécuriser votre infrastructure basée sur React.
Qu'est-ce que React2Shell (CVE-2025-55182)?
React2Shell est une vulnérabilité affectant les composants du serveur React, ainsi que les frameworks et bundles qui en dépendent, y compris Next.js, Réagir au routeur, Le vôtre, et divers plugins RSC pour Vite et Parcel. La cause première provient d'une gestion dangereuse des charges utiles sérialisées.. Lorsqu'une requête HTTP malveillante atteint un point de terminaison de fonction serveur, React désérialise la charge utile sans validation adéquate, permettant potentiellement aux attaquants d'exécuter du code arbitraire sur le serveur.
Cette vulnérabilité affecte plusieurs versions de React largement utilisées:
- 19.0.0
- 19.1.0
- 19.1.1
- 19.2.0
Et les forfaits suivants:
- réagir-serveur-dom-parcel
- réagir-serveur-dom-turbopack
- réagir-serveur-dom-webpack
Même les applications qui n'utilisent pas explicitement les composants React Server peuvent être indirectement affectées si elles s'appuient sur des bibliothèques prenant en charge RSC..

Hébergement Web WordPress
À partir de 3,99 $ / mensuel

Pourquoi React2Shell est une menace critique
La nature non authentifiée de React2Shell le rend particulièrement dangereux. Les attaquants n'ont pas besoin d'informations de connexion ni de jetons API; il leur suffit de créer une requête HTTP malveillante pour exploiter la vulnérabilité. L'impact peut inclure:
- Compromis complet du serveur
- Exfiltration de données depuis des applications vulnérables
- Déploiement de ransomwares ou de malwares dans les applications React hébergées dans le cloud
- Exploitation massive dans les campagnes d'attaques automatisées
Les chercheurs en sécurité estiment que jusqu'à 40% des environnements cloud utilisant React et Next.js peuvent être exposés, tandis que l'unité 42 rapporte près d’un million de serveurs potentiellement affectés dans le monde.
La combinaison d’une adoption généralisée et d’une gravité critique explique pourquoi une atténuation immédiate est impérative.. Selon réagir.dev:
"Un attaquant non authentifié pourrait créer une requête HTTP malveillante vers n'importe quel point de terminaison de fonction serveur qui, une fois désérialisé par React, permet l'exécution de code à distance sur le serveur.
Comment fonctionnent les composants du serveur React
Composants du serveur React (RSC) permettre aux développeurs d'exécuter certaines parties d'une application React sur le serveur tout en gardant le reste sur le client, améliorer les performances, réduire la taille des paquets, et améliorer le référencement.

Serveur VPS pas cher
À partir de 2,99 $/mois
Cependant, cette dualité introduit une surface d'attaque potentielle si les charges utiles envoyées par le client ne sont pas traitées de manière sécurisée. Le flux de travail RSC comprend plusieurs étapes clés:
- Mappage des fonctions client-serveur: Lorsqu'un client interagit avec un composant, React traduit ces appels de fonction en requêtes HTTP dirigées vers les points de terminaison du serveur. Cette abstraction permet au client de demander des données ou d'exécuter des fonctions sans exposer directement la logique du serveur..
- Exécution des fonctions du serveur: Une fois reçu, le serveur désérialise la charge utile HTTP et exécute la fonction serveur correspondante. C'est à ce stade qu'apparaît la vulnérabilité React2Shell, car une validation incorrecte des charges utiles sérialisées peut permettre aux attaquants d'injecter des instructions malveillantes, potentiellement réaliser l'exécution de code à distance.
- Retour de données: Après avoir exécuté la fonction, le serveur renvoie uniquement les données nécessaires au client. Ce transfert sélectif maintient les performances des applications et garantit une exposition minimale des données., mais si étape 2 est compromis, le serveur lui-même devient vulnérable.
En mettant en évidence le défaut à l'étape 2, il devient clair pourquoi la sécurisation de la désérialisation et la validation des charges utiles sont essentielles pour prévenir des attaques comme React2Shell.
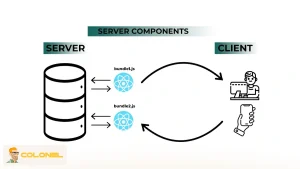
Frameworks et bundlers impactés par React2Shell
Plusieurs frameworks et bundles largement utilisés intègrent les composants React Server dans leurs flux de travail, ce qui signifie qu'une vulnérabilité dans RSC peut se propager indirectement aux applications. Les développeurs doivent examiner l’intégralité de leur arborescence de dépendances pour comprendre l’exposition potentielle et planifier les étapes d’atténuation en conséquence..
Les frameworks concernés incluent:
- Suivant.js: Connu pour le rendu côté serveur (RSS) et applications statiques hybrides, Next.js exploite RSC pour optimiser le rendu des pages. Les versions vulnérables peuvent exposer involontairement les points de terminaison du serveur aux attaquants.
- Réagir au routeur: Bien qu'il soit couramment utilisé pour le routage côté client, ses API RSC expérimentales peuvent hériter de vulnérabilités RSC.
- Le vôtre: Un framework React moderne qui s'appuie fortement sur RSC pour l'intégration dynamique serveur-client. Des instances mal configurées peuvent être exploitées via des charges utiles spécialement conçues.
Les plugins de bundler vulnérables incluent:

Hébergement VPS Windows
Remote Access & Full Admin
- @parcel/rsc
- @vitejs/plugin-rsc
- SDK séquoia (rwsdk)
Même si le code de l'application principale n'utilise pas directement les points de terminaison RSC, ces frameworks et plugins peuvent introduire des vulnérabilités, ce qui rend crucial pour les développeurs d'auditer toutes les dépendances et d'appliquer les mises à jour rapidement.
Identification des versions vulnérables
Pour déterminer si vos applications sont à risque, un audit de version détaillé est nécessaire. Cela garantit qu’aucun composant vulnérable n’est laissé sans correctif.
- Versions des composants du serveur React: La plage vulnérable est 19.0.0 à travers 19.2.0.
- Forfaits RSC: Vérifiez que réagissez-server-dom-parcel, réagir-serveur-dom-turbopack, et react-server-dom-webpack sont mis à jour vers des versions sécurisées.
- Dépendances entre pairs: Des frameworks tels que Next.js, Réagir au routeur, et Waku peut inclure ces packages RSC indirectement. La vérification de ces dépendances est essentielle pour éviter les expositions cachées.
Voici un exemple pratique d'audit de version à l'aide de npm:
- liste npm réagir-server-dom-webpack
- liste npm réagir-serveur-dom-parcel
- liste npm réagir-serveur-dom-turbopack
L'exécution de ces vérifications garantit que vous identifiez tous les composants sensibles à React2Shell et vous aide à prioriser les efforts de mise à jour des correctifs..
Stratégie d’atténuation et de mise à niveau immédiate
React a publié des versions corrigées pour tous les packages RSC vulnérables. Une action immédiate est nécessaire car les mesures d'atténuation temporaires fournies par les fournisseurs d'hébergement ne suffisent pas à sécuriser entièrement les applications..
Mises à niveau du forfait
- Packages de composants du serveur React:
- réagir-server-dom-parcel → dernière version
- réagir-server-dom-turbopack → dernière version
- réagir-server-dom-webpack → dernière version
- Mises à niveau spécifiques au framework:
- Suivant.js:
o npm install [email protected] # pour 15.0.x
o npm install [email protected] # pour 15.1.x
o npm install [email protected] # pour 15.2.x
o npm install [email protected] # pour 15.3.x
o npm install [email protected] # pour 15.4.x
o npm install [email protected] # pour 15.5.x
o npm install [email protected] # pour 16.0.x
- Réagir au routeur:
o npm install réagir@latest réagir-dom@latest réagir-server-dom-parcel@latest réagir-server-dom-webpack@latest @vitejs/plugin-rsc@latest
- SDK séquoia: Assurez-vous que rwsdk ≥ 1.0.0-alpha.0 ou utilisez la dernière version bêta.
- Plugins Waku et Vite RSC: Mettez à niveau React-Server-Dom-Webpack et les versions du plugin RSC correspondantes.
Atténuations temporaires du fournisseur d’hébergement
Alors que certains fournisseurs de cloud ont mis en œuvre des correctifs temporaires pour réduire l'exposition, se fier uniquement à ces mesures d’atténuation n’est pas sûr. Les mises à niveau immédiates des packages restent la principale défense contre l’exploitation.
Note: Pour les environnements qui reposent sur les composants React Server, en utilisant une solution VPS robuste avec un accès root complet, comme ceux proposés par le colonel Hébergement VPS géré, peut simplifier le déploiement et les tests des correctifs.
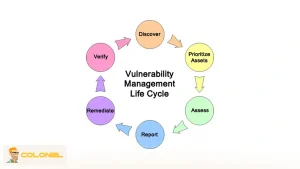
Gestion des vulnérabilités étape par étape
Gérer efficacement React2Shell nécessite une approche structurée:
- Inventorier tous les packages React: Utilisez npm ou Yarn pour identifier chaque dépendance capable de fonctionner avec la fonctionnalité RSC..
- Vérifier les versions: Vérifiez que tous les packages se situent en dehors des plages vulnérables.
- Mettre à jour les dépendances: Appliquer des versions corrigées pour éliminer l’exposition.
- Valider l'utilisation des fonctions du serveur: Évaluer si des dépendances indirectes pourraient encore exposer les points de terminaison RSC.
- Applications de test: Après la mise à jour, confirmer que l'application fonctionne comme prévu sans régression.
Suivre ces étapes garantit une réponse complète à React2Shell et réduit la probabilité de vulnérabilités résiduelles.
Mesures préventives au-delà des correctifs
Même après avoir appliqué les mises à jour nécessaires, l'adoption de solides pratiques de développement et de déploiement réduira les risques futurs liés à des vulnérabilités similaires. Les pratiques recommandées sont:
- Désactiver les fonctions de serveur inutilisées: Activez uniquement les points de terminaison côté serveur qui sont activement requis, réduire les surfaces d'attaque potentielles.
- Validation des entrées: Appliquer une validation et un assainissement stricts de toutes les données envoyées des clients au serveur, prévenir les attaques par injection.
- Mises à jour automatisées des dépendances: Des outils comme Dependabot ou Renovate peuvent détecter automatiquement les packages vulnérables et proposer des mises à jour.
- Audits de codes: Examinez périodiquement les packages tiers pour détecter les modèles de désérialisation dangereux et d'autres problèmes de sécurité..
Ces mesures complètent les correctifs et créent une architecture d'application plus résiliente.
Leçons de React2Shell
L'incident React2Shell met en lumière des leçons cruciales pour les développeurs et les organisations travaillant avec des frameworks Web modernes:
- La complexité engendre des vulnérabilités: Les frameworks hybrides serveur-client comme RSC introduisent de nouveaux vecteurs d'attaque potentiels.
- Les dépendances indirectes comptent: Les applications peuvent être vulnérables même sans utilisation directe des points de terminaison RSC si les packages dépendants les incluent.
- Le déploiement rapide des correctifs est essentiel: Vulnérabilités de grande gravité (CVSS 10) exiger immédiatement, action à l’échelle de l’organisation pour minimiser les risques.
Exemple: Une plateforme SaaS gérant plusieurs applications Next.js pourrait automatiser le déploiement de correctifs via des pipelines CI/CD. Cette approche réduit les erreurs humaines, garantit des mises à jour de sécurité cohérentes, et atténue l'exposition aux attaques comme React2Shell.
Conclusion
Réagir2Shell (CVE-2025-55182) représente une vulnérabilité RCE critique dans l’écosystème React, affectant particulièrement les composants serveur et les frameworks associés. La combinaison d’un accès non authentifié, adoption généralisée, et un CVSS 10 la notation en fait une priorité absolue en matière de sécurité. Les mesures immédiates comprennent:
- Mise à niveau de tous les packages RSC vulnérables
- Mise à jour des frameworks et plugins concernés
- Validation de l'utilisation des fonctions du serveur
- Utiliser des pratiques de codage préventives
En gérant de manière proactive ces mises à jour et en mettant en œuvre des pratiques sécurisées, les développeurs peuvent maintenir une résilience, performant, et environnement sécurisé basé sur React.
FAQ sur les vulnérabilités React2Shell et RSC
Mon application React est-elle vulnérable si je n'utilise pas les fonctions du serveur?
Si votre application et ses dépendances n'implémentent pas les composants React Server ou les points de terminaison des fonctions serveur, ce n'est pas affecté. Cependant, vérifiez toujours les dépendances indirectes.
À quelle vitesse dois-je appliquer les correctifs?
Immédiatement. CVSS 10 les vulnérabilités sont critiques, et tout retard augmente le risque d'exploitation.
Le fournisseur d'hébergement est-il’s atténuations suffisantes?
Non. Les correctifs temporaires peuvent réduire l’exposition mais ne peuvent pas empêcher complètement les attaques. La mise à jour des dépendances est obligatoire.
Les outils automatisés peuvent-ils aider à prévenir de futures vulnérabilités?
Oui. Des outils comme Dependabot, Rénover, et l'audit npm peut automatiquement notifier et mettre à niveau les packages vulnérables.
Quels frameworks sont concernés en dehors de React?
Suivant.js, Réagir au routeur, Le vôtre, SDK séquoia, et certains plugins Vite/Parcel RSC sont impactés.
