Site Web gratuit & Serveur Migration
Blog
Install and Configure OpenVPN Access Server VPN
OpenVPN Access Server is a powerful and easy-to-use VPN solution that is designed to offer a secure and reliable way to access a private network from the internet. OpenVPN Access Server is a powerful solution that offers a combination of strong encryption, flexible authentication, and easy management ...
Colonelserver vs Hostinger – Features, Vitesse & Prix
In comparing Colonelserver vs Hostinger, both hosting companies have features that are beneficial, but overall, Colonelserver has better performance and more advanced features that will appeal to users with more demanding needs. Hostinger is liked for its budget-friendly pricing and ease of use, while Colonelserver is expected ...
AI Crawlers vs robots des moteurs de recherche dans 2026: Quoi 66 Un milliard de demandes de robots révélées
AI crawlers are expanding their footprint across the web faster than any other category, while traditional search engine bots remain structurally dominant, and LLM training bots face increasing resistance. An analysis of 66.7 billion bot requests across more than five million websites shows that the web is ...
Docker & Guide complet de la sécurité des conteneurs Kubernetes
Docker & Kubernetes container security is the structured practice of protecting container images, orchestration layers, and runtime environments from vulnerabilities, mauvaises configurations, and active threats across the entire container lifecycle. As organizations increasingly rely on containers for scalable cloud-native applications, understanding Docker & Kubernetes container security is no ...
Renforcez la sécurité des e-mails avec SPF, Dkim, DMARC
Email authentication has emerged as a very important aspect of securing communication, and businesses can no longer depend on simple spam filters alone. FPS, Dkim, and DMARC are protocols that work in tandem to ensure the authenticity of the sender, prevent domain spoofing, and increase the authenticity ...
Les pirates ciblent le déploiement de l’IA comme étant terminé 91,000 Les sessions d'attaque sont découvertes
Sur 91,000 attacks on AI infrastructure were documented in a synchronized attack on artificial intelligence deployment from October 2025 to January 2026. The security telemetry gathered from honeypot sensors worldwide validates the existence of two structured attacks targeting server-side request forgery vulnerabilities and probing large language model ...
Services d'hébergement de conteneurs Docker sécurisés
Docker Container Hosting is an essential part of today’s application hosting, particularly when security is the number one concern. Secure Docker Container Hosting Services offer isolated environments, sophisticated threat protection, automated patching, and robust access controls to protect microservices and cloud-native applications. By leveraging the efficiency of ...
VPS Kali Linux: Pouvoir, Confidentialité, et flexibilité Go
Le VPS Kali Linux offre une forte, sécurisé, and highly flexible platform for professionals who require complete control over their penetration testing, cybersecurity, and development work. With the Kali Linux VPS, users can enjoy remote access to a dedicated platform that provides high performance and increased privacy, ...
ColonelServer vs Bluehost - Comparaison complète d'hébergement
A good hosting solution is an essential part of a website’s performance and functionality. This ColonelServer vs Bluehost comparison is centered around the differences that matter to actual users, such as server performance, allocation des ressources, pricing model, et flexibilité technique. Although both solutions are popular and widely ...
Le bug OpenClaw permet l'exécution de code à distance en un clic par un lien malveillant
La divulgation du CVE-2026-25253 a soulevé de sérieuses inquiétudes au sein de la communauté de la cybersécurité après que les chercheurs ont confirmé qu'un bug d'OpenClaw permettait l'exécution de code à distance en un clic via un lien malveillant spécialement conçu.. Le défaut de haute gravité, affectant la plate-forme d'agents d'IA open source à croissance rapide OpenClaw (formerly Clawdbot and Moltbot), allows attackers ...
Serveurs dédiés alimentés par GPU pour une charge de travail extrême
GPU-Powered Dedicated Servers for extreme computing workloads have revolutionized the way organizations process compute-intensive tasks like AI model training, big data processing, 3Rendu D, et analyses en temps réel. By leveraging the sheer processing power of GPUs with the reliability and resource utilization capabilities of dedicated servers, these servers ...
Mise à l'échelle de WordPress Kubernetes pour les sites Web natifs du cloud à fort trafic
WordPress Kubernetes scaling is the most effective way to run WordPress in a cloud-native architecture that can handle millions of visitors without performance degradation. Traditional single-server deployments struggle to cope with sudden traffic spikes, but combining containerization with orchestration enables horizontal scalability, resilience, and operational consistency.
Dans ce ...
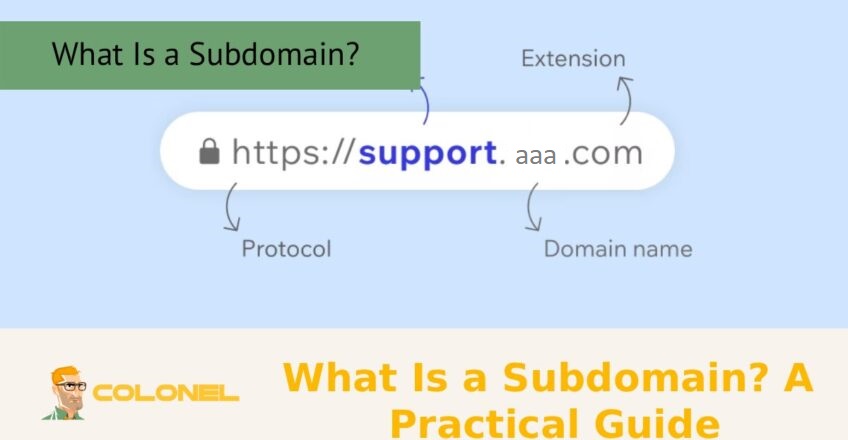
Qu'est-ce qu'un sous-domaine? Un guide pratique
Qu'est-ce qu'un sous-domaine? A practical guide to understanding how subdomains work and why they matter for modern websites. A subdomain is a separate section of your main domain that helps you organize content, create distinct site areas, or target different audiences without purchasing a new domain ...
Meilleures distributions Linux pour serveurs virtuels
Best Linux Distributions for Virtual Servers play a crucial role in building stable, sécurisé, et des environnements d'hébergement performants. Choosing the right distribution can directly impact server efficiency, resource management, évolutivité, and long-term maintenance costs. Whether you are running a VPS platform, managing enterprise workloads, or deploying cloud-based ...