
Recovering a hijacked domain online requires fast, structured action backed by technical verification and registrar-level escalation. When a domain is hijacked, access to your website, email, and digital identity can disappear instantly, putting both revenue and credibility at risk. Understanding how domain hijacking works and knowing the correct way to recover hijacked domains online dramatically increases the chances of regaining control before permanent damage occurs.
What Is Domain Hijacking and How Do You Recognize It?
Domain hijacking is the unauthorized takeover of a domain name through changes to ownership records, DNS settings, or registrar access. This attack typically occurs without warning and often becomes visible only after services fail or traffic is redirected. ICANN states:
“Unauthorized transfers undermine trust in the domain name system, and registrars are required to investigate and act under established transfer dispute policies.”
Early detection plays a decisive role in recovering hijacked domain online scenarios because registrars can reverse changes more easily before a domain is transferred again. Many domain owners initially misdiagnose hijacking as a hosting issue, which wastes critical time.
Common indicators of domain hijacking include unexpected DNS changes, inability to log in to the registrar dashboard, altered WHOIS contact details, and reports from users that the website or email services are unreachable. Any combination of these signals should trigger immediate investigation.


WordPress Web Hosting
Starting From $3.99/Monthly
How Does Domain Hijacking Usually Happen?
Domain hijacking follows a predictable operational pattern driven by weak authentication, human error, or expired registrations. Attackers rarely rely on a single exploit and instead combine technical and psychological tactics.
Most incidents begin with credential compromise through phishing or social engineering. Once access to the registrar account is obtained, attackers modify registrant data and initiate a domain transfer to a foreign registrar, complicating recovery. The typical hijacking workflow includes:
- Credential theft via phishing emails impersonating registrars or internal staff
- Unauthorized changes to WHOIS contact information
- Transfer of the domain to another registrar or owner
- Abuse of the domain for phishing, malware distribution, resale, or traffic monetization
Understanding this chain of events helps domain owners interrupt the process early and recover hijacked domains online before escalation becomes legally complex.
Immediate Risks After a Domain Is Hijacked
A hijacked domain does not only affect website availability; it undermines every digital service tied to that domain. Email delivery fails, SSL certificates become invalid, and customer trust erodes rapidly.
Search engine rankings can also suffer lasting harm if attackers serve malicious or spam content. Even after recovery, blacklisting by browsers or email providers may persist, extending the impact well beyond the hijacking event.
For businesses, the financial consequences include lost sales, customer churn, regulatory exposure, and reputational damage. This is why domain hijacking should be treated as a security incident rather than a simple administrative issue.

Cheap VPS Server
Starting From $2.99/Monthly
Step-by-Step Strategy to Recover Hijacked Domains Online
Recovering a hijacked domain online depends on speed, documentation, and registrar cooperation. The first 24 hours are often decisive because many registrars can reverse unauthorized changes before secondary transfers occur.
This process requires technical verification, identity proof, and escalation through proper channels. Skipping steps or acting informally reduces recovery success rates.

Step 1: Confirm the Domain Hijack
Verification is essential before initiating ‘recover hijacked domains online procedures’. Technical outages can resemble hijacking but require different solutions.
Start by performing a WHOIS lookup through trusted services such as ICANN Lookup or registry-specific tools. Compare current registrant, administrative, and technical contact data with historical records and invoices.
If ownership details, registrar name, or nameservers differ from your records, the domain has likely been hijacked. At this stage, document everything, including timestamps, screenshots, payment confirmations, and archived WHOIS data to support your claim.

Windows VPS Hosting
Remote Access & Full Admin
Step 2: Secure All Related Accounts Immediately
Once hijacking is confirmed, assume credential compromise beyond the registrar account. Email access is particularly critical because it often controls password resets.
Change passwords for the registrar account, associated email addresses, and hosting dashboards using long, unique credentials. Enable two-factor authentication wherever available, preferably using app-based authenticators rather than SMS.
This containment step prevents attackers from regaining access during the process of recovering a hijacked domains online and strengthens your position when working with registrars or legal authorities.

Step 3: Contact Your Domain Registrar Without Delay
The registrar is the primary authority capable of reversing unauthorized domain actions. Contacting them directly is the most effective way to recover hijacked domains online.
Phone communication is strongly preferred because email responses can be delayed or intercepted. Request escalation to the abuse or security department and clearly state that your domain was transferred or modified without authorization.
Be prepared to provide ownership proof such as billing history, government-issued identification, and prior WHOIS records. Ask the registrar to apply an immediate transfer lock and investigate under ICANN’s Transfer Dispute Resolution Policy.
Step 4: Determine Whether the Domain Was Transferred
The path to recover hijacked domains online depends on whether the domain remains with the original registrar or has been transferred elsewhere. WHOIS data reveals the gaining registrar if a transfer occurred.
If the domain remains internal, recovery can often be completed within days. If transferred, coordination between registrars becomes necessary, increasing complexity and timelines.
Understanding this distinction early allows you to escalate correctly and prevents procedural delays that reduce the chance of recovering a hijacked domain online successfully.
Escalation Paths When the Registrar Cannot Immediately Help
Recovering a hijacked domain online sometimes requires moving beyond standard registrar support, especially when the domain has already been transferred or when cooperation is limited. In these cases, escalation through formal technical and legal channels becomes unavoidable.
This escalation is not about reacting emotionally, but about following structured procedures defined by ICANN and domain registries. The earlier these steps are initiated, the higher the likelihood of reversing unauthorized changes.
Filing a Transfer Dispute Under ICANN Policies
When a domain transfer occurs without the owner’s approval, ICANN’s Transfer Dispute Resolution Policy provides a defined mechanism to challenge that transfer. This process obligates registrars to investigate whether proper authorization was obtained. Key actions in a transfer dispute include:
- Submit formal proof of ownership to the losing registrar, such as payment records, historical WHOIS data, and account access logs, to establish that the transfer was unauthorized.
- Requesting a registrar-to-registrar investigation, which forces both parties to review authorization records and transfer approvals
- Referencing ICANN’s Transfer Policy explicitly, ensuring the case follows standardized compliance rules rather than discretionary support decisions
This path is especially effective when you act quickly to recover hijacked domains online before the domain is resold or transferred multiple times.

Using UDRP for Legal Domain Recovery
When registrar-based way to recover hijacked domains online fails, or the hijacker refuses to cooperate, the Uniform Domain-Name Dispute-Resolution Policy becomes the most effective legal route. UDRP provides a structured alternative to court litigation and applies globally.
UDRP is particularly relevant for businesses, brands, and organizations with trademark rights. It focuses on intent, legitimacy, and bad-faith use rather than technical ownership alone. To succeed in a UDRP case, you must clearly demonstrate:
- Trademark similarity, meaning the disputed domain closely matches a trademark you legally own or represent
- Lack of legitimate interest, showing the current holder has no valid reason to use the domain.
- Bad-faith registration or use, such as phishing, resale attempts, impersonation, or traffic diversion
Although this process takes longer than registrar intervention, it remains one of the most reliable methods to recover hijacked domains online when ownership disputes escalate.
Types of Domain Hijacking You Should Be Aware Of
Domain hijacking is not a single attack method, but a group of takeover techniques that target different weaknesses in domain ownership, authentication, and DNS control. Identifying the exact type of hijacking is critical because recovery strategies and escalation paths depend heavily on how the domain was compromised.
Below are the most common and impactful types of domain hijacking encountered in real-world recovery cases.
Registrar Account Hijacking
Registrar account hijacking is the most common and fastest form of domain takeover. In this scenario, attackers gain access to the domain owner’s registrar account, typically through phishing, credential reuse, or compromised email accounts.
Once inside the account, the attacker can change WHOIS data, update DNS records, disable domain locks, and initiate transfers without triggering immediate alarms. Because the attacker operates from within the legitimate control panel, this type of hijacking often goes unnoticed until services fail. Recovery is usually possible if detected early, especially before a registrar-to-registrar transfer is completed.
Unauthorized Domain Transfer Hijacking
This type of hijacking occurs when a domain is transferred to another registrar without the owner’s consent. Attackers exploit stolen authorization codes, weak transfer verification, or compromised registrar credentials to move the domain outside the original provider’s control.
Unauthorized transfers significantly complicate recovery because they introduce a second registrar and jurisdiction into the process. At this stage, recovering a hijacked domain online often requires ICANN Transfer Dispute Resolution procedures rather than standard support tickets. Timing is critical, as multiple transfers reduce the likelihood of a clean reversal.
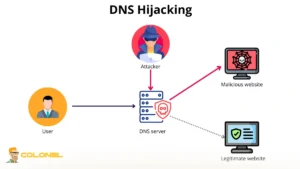
DNS Hijacking Without Ownership Transfer
DNS hijacking targets the domain’s nameserver configuration rather than its ownership records. The attacker redirects traffic by modifying A, MX, or CNAME records, while the domain technically remains under the rightful owner’s name.
This attack is frequently used for phishing, credential harvesting, or malware distribution, as it allows attackers to impersonate legitimate websites and email services. DNS hijacking is especially dangerous because domain owners may focus on hosting or server issues, delaying proper investigation. The process to recover hijacked domains online usually involves restoring DNS records and securing registrar access rather than legal escalation.
WHOIS Data Manipulation Hijacking
In this scenario, attackers alter WHOIS registrant, administrative, or technical contact information without immediately transferring the domain. This change is often a preparatory step before a full hijack or transfer.
By replacing contact details, attackers intercept recovery emails, transfer confirmations, and security alerts. Domain owners who rely on outdated WHOIS data may lose control gradually without realizing it. Early detection of unauthorized WHOIS changes can prevent escalation and simplify efforts to recover hijacked domains online.
Expired Domain Hijacking
Expired domain hijacking occurs when a domain lapses due to missed renewal and is quickly re-registered or acquired by a third party. While technically not always illegal, it has the same operational impact as malicious hijacking.
Attackers and domain brokers monitor expiration windows closely, especially for high-value domains. Once the domain is re-registered, recovery options become limited and may require negotiation or legal action rather than registrar intervention. Long-term renewals and auto-renewal settings are the most effective defense against this type of takeover.
Insider or Registrar-Level Hijacking
Although rare, some cases involve insider abuse at registrars or resellers, where internal access is misused to alter ownership or transfer domains. These incidents are difficult to detect early and often require formal investigations.
Recovery in such cases typically depends on documented ownership history, billing records, and escalation through ICANN compliance channels. While uncommon, this type of hijacking highlights why domain governance should be treated as a security-critical process rather than a simple administrative task.
Why Identifying the Hijacking Type Matters
Understanding which type of domain hijacking occurred directly determines the fastest and most effective strategy to recover hijacked domains online. Registrar account compromises can often be reversed internally, while unauthorized transfers require formal disputes.
DNS-only hijacks demand technical remediation rather than legal escalation.
Misidentifying the attack type leads to wasted time, incorrect escalation, and lower success rates when attempting to recover hijacked domains online. Accurate classification is therefore the foundation of any successful recovery effort.
Expected Recovery Timelines in Real Situations
Domain recovery timelines vary widely depending on detection speed, registrar cooperation, and legal involvement. Understanding realistic expectations helps plan communication and mitigation strategies.
| Scenario | Typical Recovery Time |
| Detected within 24 hours, same registrar | 1–3 days |
| Transferred, registrar dispute required | 7–21 days |
| UDRP legal process | 45–60 days |
| Court litigation | 6–12 months |
Early detection remains the strongest factor influencing recovery speed and success.
Securing Your Domain After Successful Recovery
Recovering access alone does not eliminate risk. A previously hijacked domain must be treated as compromised until its security posture is fully restored and verified.
Post-recovery hardening should include:
- Activating registrar and registry locks, preventing any transfer or ownership change without manual verification
- Reviewing and correcting WHOIS records, ensuring all contact information reflects authorized owners only
- Restoring and validating DNS configurations, including A, MX, and CNAME records, to eliminate malicious routing
- Enabling DNSSEC, which protects DNS integrity and prevents record manipulation
- Renewing the domain for multiple years, reducing the risk of expiration-based hijacking
These steps convert recovery into long-term stability rather than temporary control.

Preventive Strategies to Avoid Domain Hijacking Recurrence
Preventing hijacking is significantly easier and less costly than attempting to recover hijacked domains online after an incident. Most hijacks exploit weak operational controls rather than advanced technical vulnerabilities. Effective prevention includes:
- Using strong, unique passwords stored in a password manager eliminates credential reuse risks.
- Enabling two-factor authentication on registrar and email accounts, which blocks most account takeover attempts
- Maintaining permanent domain lock status, unlocking only when an intentional transfer is required.
- Using a dedicated private email for domain management reduces exposure to phishing campaigns.
- Monitoring WHOIS and DNS changes continuously, allowing immediate detection of unauthorized modifications.
Organizations that apply these practices significantly reduce hijacking risk while improving recovery readiness.
Turning Domain Recovery into Long-Term Control
Recovering a hijacked domain online is not just a technical challenge but an operational test of preparedness and response discipline. Domains represent critical infrastructure, and loss of control directly affects trust, visibility, and business continuity.
When recovery actions align with registrar policies, legal frameworks, and proactive security controls, organizations move from reactive damage control to sustainable domain governance. The real success lies not only in regaining access, but in ensuring it never happens again.
Frequently Asked Questions
Can a hijacked domain really be recovered online?
Yes, many hijacked domains can be recovered online if action is taken quickly and ownership evidence is available. Registrar cooperation is the most important factor.
What if the attacker transferred the domain abroad?
International transfers complicate recovery but remain reversible through ICANN disputes or UDRP procedures, especially within early transfer windows.
Does enabling domain lock guarantee protection?
Domain lock significantly reduces risk but must be combined with strong account security and email protection to remain effective.
How long should I wait before escalating legally?
If registrar-level recovery fails within days, escalation through ICANN or UDRP should begin immediately to preserve recovery options.
Is paying the hijacker ever recommended?
Negotiation may be a last resort when business continuity depends on the domain, but it carries legal and ethical risks and should involve legal counsel.
