
The decision by Let’s Encrypt to shorten the maximum certificate validity from 90 days to 45 days marks one of the most influential structural changes in the modern TLS ecosystem. This update is not an isolated event but part of a broader movement by the CA and browser communities to strengthen protection against compromise, reduce reliance on traditional revocation, and encourage fully automated certificate lifecycle management.
Understanding this transition is essential for administrators, DevOps teams, developers, and security engineers who design systems that depend on uninterrupted HTTPS availability. This article provides a comprehensive analysis of the policy changes, the validation timeline, operational implications, automation challenges, and the ACME client behavior that Let’s Encrypt now expects.
Why Let’s Encrypt Is Moving to 45 Day Certificates
The primary reason for this transition is to narrow the exposure window for leaked or stolen private keys. Shorter SSL Certificate lifetimes significantly reduce the time a compromised key can be abused, especially in cases where revocation mechanisms are slow or unreliable.
This shift aligns with new Baseline Requirements from the CA and Browser Forum. These requirements aim to improve end-to-end trust by ensuring that certificates remain continuously tied to current and validated domain owners. As a result, certificate authorities must shorten validity periods and require more frequent authorization checks.
The following outcomes are the direct security benefits of this reduction:
- It limits the operational usefulness of stolen private keys since the certificate becomes invalid more quickly.
- It improves the reliability of revocation systems because smaller validity windows reduce the pressure on external revocation mechanisms.
- It forces organizations to upgrade and automate certificate lifecycle management, which historically has been a major source of expired certificate outages.
Understanding the Reduction in Authorization Reuse Period
The reduction in certificate lifetime is deeply connected to the change in authorization reuse. Authorization reuse defines how long a previously validated domain can skip revalidation. Let’s Encrypt currently supports a thirty-day reuse period, which allows administrators to renew certificates once a month without revalidating domain ownership.

WordPress Web Hosting
Starting From $3.99/Monthly
The main reasons behind this change can be summarized as follows:
- Attackers who gain access to an ACME account or DNS configuration will not be able to maintain long-lived certificate issuance using stale authorizations.
- Revocation and authorization caching become more effective because any compromise has a very limited time window.
- It improves parity between automated and static DNS environments, encouraging teams to adopt more secure and automated workflows.
Here’s the letsencrypt official announcement:
“Let’s Encrypt will shorten certificate maximum validity from 90 days to 45 days and reduce the authorization reuse period, reducing the window of compromise and improving revocation efficacy.”
Full Let’s Encrypt Rollout Timeline for the 45 Day Certificates
Let’s Encrypt will not apply these changes suddenly. Instead, it is using ACME profiles to gradually roll out the new lifetimes. This structured approach reduces operational risk and allows developers and administrators to test their automation pipelines before the changes become mandatory.
The official timeline includes three major phases. Understanding this timeline is essential because renewal policies, validation requirements, and client expectations shift at every phase.

Cheap VPS Server
Starting From $2.99/Monthly
Phase One: May 13, 2026
In this phase, Let’s Encrypt will introduce the tlsserver ACME profile. This profile issues certificates with a maximum validity of 45 days and is designed for early adopters and teams that want to validate their automation strategies before mandatory enforcement. The main characteristics of this phase include:
- The changes are opt-in, so production environments can remain unaffected while testing.
- Teams can evaluate how their ACME clients respond to the shorter lifetime.
- Developers can identify issues related to DNS updates, rate limits, scheduling, and automated reloads.
Phase Two: February 10, 2027
During this phase, the default classic profile will begin issuing sixty four day certificates rather than the ninety day certificates used today. Authorization reuse will also be limited to ten days rather than thirty.
The following effects will be visible across most infrastructures:
- Legacy renewal scripts based on sixty day intervals will cause outages because they will allow certs to expire before renewal.
- ACME clients that do not support dynamic scheduling will need to be upgraded.
- DNS-01 workflows that depend on slow manual updates will begin failing.
Phase Three: February 16, 2028
This phase completes the transition. All certificates will be restricted to a maximum of 45 days, and domain authorizations will only remain valid for seven hours. This final change introduces several operational requirements that every administrator must prepare for:
- DNS challenges require near instant automation; otherwise, validation attempts will fail.
- Certificate renewals must run much more frequently.
- Human involvement becomes impractical because renewals occur every few weeks.

Why Hardcoded Renewal Intervals Will Break After the Transition
Many organizations still rely on simple cron jobs set to run once every sixty days. This pattern worked for ninety-day certificates, but it becomes incompatible with the new shortened lifetime. Certificates will expire before the renewal script ever runs, resulting in production outages.

Windows VPS Hosting
Remote Access & Full Admin
The main renewal guidance from Let’s Encrypt is straightforward: automatic clients should renew certificates at approximately two-thirds of the certificate lifetime. For a forty five day certificate, the two thirds point occurs around day thirty. That requires renewal automation that runs frequently and reliably.
The Importance of ACME Renewal Information (ARI)
To support administrators during this transition, Let’s Encrypt recommends enabling ACME Renewal Information. ARI is a mechanism that allows the certificate authority to signal the optimal renewal time directly to the ACME client. This feature helps avoid premature renewals, prevents mass simultaneous renewals during outages, and spreads load evenly across the ecosystem.
ARI also allows renewal behavior to adapt when policies change. This eliminates the need for administrators to adjust complex scheduling logic manually.
If your ACME client supports ARI, you should enable it immediately. If it does not, you should plan to migrate to a modern client or upgrade your existing one.
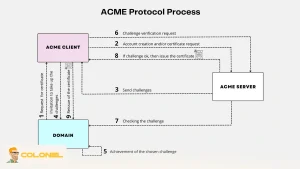
Why Manual Certificate Management Is No Longer Feasible
The reduced certificate lifetime creates a significant burden for teams that rely on manual certificate issuance. Renewals will occur roughly every month, and domain validation will need to be repeated frequently. Human workflows simply cannot support this workload.
This change forces organizations to adopt automated, scriptable, and repeatable processes for certificate issuance and deployment. Failing to automate will lead to expired certificates, service interruptions, and possibly security incidents.
How DNS-PERSIST-01 Will Transform Domain Validation
The introduction of DNS-PERSIST-01 will fundamentally improve domain validation for environments where DNS updates cannot be automated. Today, DNS-01 requires a new TXT record for each renewal. This is problematic for infrastructures where DNS modifications require approval or can only be done manually.
DNS-PERSIST-01 solves this by allowing a single static DNS TXT entry that remains valid indefinitely. Once the first verification is completed, future validations do not require additional changes. This enables seamless automated renewals even in environments where DNS cannot be modified easily.
This new method is expected to benefit the following categories of deployments:
- Enterprises using DNS providers without APIs
- Legacy systems with fixed DNS management processes
- Environments where DNS changes propagate slowly
- Teams that outsource DNS and cannot easily modify the zone
DNS-PERSIST-01 is expected to be standardized and launched in 2026. Organizations should follow the development of this method carefully because it may completely eliminate many of the operational limitations associated with DNS-01.
How to Adapt Your Infrastructure for the 45 Day Certificates
Preparing your infrastructure for shorter certificate lifetimes requires a structured and systematic approach. The goal is to ensure smooth renewals, predictable behavior, and complete elimination of human errors.
Below is a comprehensive multi step process that ensures your organization is fully prepared for the transition.
Step One: Inventory All Certificates
Your first step should be a complete inventory of all certificates across all environments. This includes production, staging, internal systems, APIs, microservices, and administrative dashboards. Many outages occur because hidden or forgotten certificates do not renew automatically.
The inventory should include the following fields:
- Domain names covered
- Validation method used
- ACME client version
- Renewal schedule
- Deployment method
- Dependency chains such as load balancers and reverse proxies
Step Two: Upgrade ACME Clients
The second step is to ensure all ACME clients support modern standards such as ARI, ACME profiles, and the upcoming validation updates. Older clients will fail when confronted with reduced authorization reuse or shortened validity.
Step Three: Automate All DNS Updates
If your environment depends on DNS-01 validation, automation is essential. Use DNS providers that offer comprehensive APIs and integrate these APIs into your ACME client.
Automated DNS updates protect against interruptions caused by slow propagation, slow approvals, or manual intervention.
Step Four: Update Renewal Schedules
Adjust your renewal schedules to run weekly or twice weekly. The ACME client will only renew when appropriate, so frequent checks do not increase load.
Many administrators also choose to stagger renewal attempts across different servers to avoid rate limits.
Step Five: Enhance Monitoring and Alerting
The last step is to enhance monitoring and alerting systems. Certificate expiration checks must be integrated into your observability stack. Alerts should trigger long before certificates are near expiration.

Example of a Robust Automated Renewal Workflow
A practical design for a reliable renewal workflow involves system services that execute checks on a regular basis. These services then trigger web server reloads only when necessary. A typical workflow includes:
- A timer that runs twice per week to trigger the ACME client
- A renewal check that evaluates expiration and ARI guidance
- Conditional certificate issuance
- Automatic deployment of the new certificate
- Automatic reload of the reverse proxy or web server.
This workflow eliminates the risk of outages and requires no manual intervention.
Example Scenario: Migration for a Medium-Scale Web Hosting Company
To illustrate the challenges and solutions, consider a hosting provider that manages certificates for more than twenty thousand customer sites. Many customers use custom domains with DNS provided by multiple external vendors. Before adopting the new policies, the provider must implement:
- An internal DNS automation engine that supports a wide range of DNS APIs
- A distributed certificate management layer that uses ARI to avoid spikes
- A certificate deployment pipeline that integrates with the hosting control panel
- A fail-safe monitoring system that checks expirations across all virtual hosts
This example demonstrates how complex environments can benefit from large-scale automation that reduces operational risk.
Conclusion
Let’s Encrypt’s shift to shorter certificate lifetimes and a far shorter authorization reuse window accelerates the need for resilient automation and better DNS integration. By upgrading ACME clients, adopting ARI, preparing for DNS persistence, and implementing robust monitoring and renewal orchestration, you can avoid outages and improve security posture.
Start with inventorying certificates, upgrade tooling, test renewals in staging, and implement daily checks and alerting to be ready well before final enforcement.
Frequently Asked Questions
Why is Let’s Encrypt reducing certificate lifetimes?
Let’s Encrypt is reducing certificate lifetimes to improve security by limiting the usefulness of compromised keys and strengthening the effectiveness of revocation systems.
Will these changes increase the load on administrators?
They increase the need for automation, but once automation is deployed correctly, the workload actually decreases because the process becomes predictable and fully hands off.
What happens if I keep using my sixty day cron job?
Your certificates will expire before renewal and cause service outages. You must update your schedule to run much more frequently.
Is DNS-PERSIST-01 required?
It is not required, but it is highly recommended for environments where DNS cannot be updated programmatically.
When will DNS-PERSIST-01 be available?
It is expected to launch in 2026, after the IETF finalizes the new validation standard.
