The TGR-STA-1030 cyber espionage operation has affected a minimum of 70 government and critical infrastructure entities in 37 countries during the last year. As per research published by Palo Alto Networks Unit 42, the newly discovered threat actor has been actively engaged in intelligence gathering activities since 2024 and 2025, targeting government ministries, law enforcement agencies, and entities that support economic and political missions. The extent of this operation places TGR-STA-1030 cyber espionage among the most dangerous state-sponsored campaigns that are presently active.
Experts believe that the threat actor is of Asian origin, given the toolset characteristics, operation timing that is consistent with GMT+8, language settings, and target entity priorities that are regionally consistent.
Extensive Reconnaissance Across 155 Countries
In addition to the confirmed intrusions, the TGR-STA-1030 cyber espionage campaign involved active reconnaissance against government infrastructure in 155 nations during November and December 2025. The scale of this scanning attack suggests a systematic intelligence-gathering pipeline instead of sporadic breaches. Among the confirmed victims:
- Five national-level law enforcement and border control organizations
- Three ministries of finance
- Various ministries for economic, trade, natural resources, and foreign affairs
The scope of the attack suggests systematic intelligence gathering instead of financially driven cybercrime. Reports show that the group has been active since at least January 2024. Pete Renals, Director of National Security Programs, commented:
“The threat actor successfully accessed and exfiltrated sensitive data from victim email servers.” _The Hacker News
The compromised data consisted of financial negotiation data, contracts, banking information, and military operation updates, which highlights the geopolitical nature of the attack.

WordPress Web Hosting
Starting From $3.99/Monthly
Initial Access: Phishing and Diaoyu Loader Malware
The TGR-STA-1030 cyber espionage campaign commonly began with phishing emails containing a link to a ZIP archive hosted on the New Zealand-based file-sharing service MEGA. The archive included an executable known as Diaoyu Loader and a zero-byte PNG file named “pic1.png.”
Diaoyu Loader incorporates a dual-stage execution guardrail designed to evade automated sandbox analysis. The malware checks for:
- A minimum screen resolution of 1440 pixels horizontally
- The presence of “pic1.png” within its execution directory
If the PNG file is absent, the malware terminates, effectively bypassing automated security analysis environments that fail to replicate the exact file structure. (Visit Our Hacked Website Repair Service)

Security Software Evasion and Payload Delivery
After passing its environmental checks, Diaoyu Loader searches for specific cybersecurity products, including:
- Avira
- Bitdefender
- Kaspersky
- SentinelOne
- Symantec
The narrow focus on these vendors suggests targeted evasion logic rather than broad antivirus detection routines. Once conditions are satisfied, the loader retrieves three image files from a GitHub repository masquerading as “WordPress.” These images function as covert payload containers.

Cheap VPS Server
Starting From $2.99/Monthly
Cobalt Strike is ultimately deployed as the primary command-and-control framework. The GitHub account used in the operation has since been removed, indicating attempts to erase forensic artifacts.
The use of legitimate platforms for payload staging demonstrates operational discipline consistent with state-aligned threat actors.
Exploitation of N-Day Vulnerabilities
In addition to phishing, TGR-STA-1030 cyber espionage operations leveraged multiple N-day vulnerabilities across widely deployed enterprise platforms, including products from:
- Microsoft
- SAP
- Atlassian
- Ruijieyi Networks
- Commvault
- Eyou Email System
Notably, investigators found no evidence of zero-day exploitation. Instead, the group capitalized on unpatched systems, highlighting persistent patch management weaknesses across government networks.
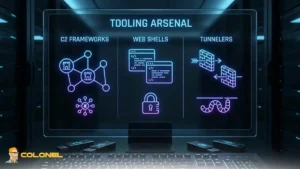
Tooling Arsenal: C2 Frameworks, Web Shells, and Tunnelers
The operational maturity of the TGR-STA-1030 campaign is reflected in its carefully curated post-exploitation toolkit. Rather than relying on bespoke malware alone, the group leveraged widely used offensive security frameworks, stealthy web shells, and tunneling utilities to maintain persistence and evade detection across compromised government and critical infrastructure networks.
This diversified tooling stack suggests a structured operational model consistent with long-term cyber espionage campaigns. The TGR-STA-1030 cyber espionage toolkit includes a diverse and mature set of post-exploitation utilities:

Windows VPS Hosting
Remote Access & Full Admin
Command-and-Control Frameworks
TGR-STA-1030 utilized several command and control (C2) infrastructures to manage the delivery of payloads, lateral movement, and remote task execution within the compromised environments. The employment of multiple C2 infrastructures enhances the threat actor’s ability to switch between the infrastructures in case one of them is detected or disabled.
- Cobalt Strike: This infrastructure is commonly used by state-sponsored actors to facilitate communication through beacons, privilege escalation, and in-memory execution, which helps to minimize forensic evidence.
- VShell: This is a remote access utility that can be used to establish and maintain persistent command and control channels.
- Havoc: This is an open-source post-exploitation framework that aims to replicate advanced red team tradecraft.
- Sliver: This is a cross-platform adversary simulation framework that supports encrypted communication and staged payload delivery.
- SparkRAT: This is a remote access trojan that has the capability to execute commands on multiple platforms and monitor the compromised environment.
The employment of multiple C2 infrastructures in the TGR-STA-1030 cyber espionage campaign indicates a redundancy approach that makes the threat actor less dependent on any of the infrastructure components.
Web Shells
Web shells were an important part of the process of creating stealthy footholds in the compromised web-facing infrastructure. These lightweight backdoors enable attackers to run commands via HTTP requests, making malicious traffic indistinguishable from normal web traffic patterns.
- Behinder: A known encrypted web shell commonly attributed to Chinese-speaking actors.
- neo-reGeorg: Often used to pivot traffic into internal networks via SOCKS proxy tunneling.
- Godzilla: A modular web shell featuring encryption and plugin-based extensibility.
The presence of these particular web shells does increase the regional attribution confidence related to the TGR-STA-1030 activities, especially in light of their regular use in campaigns that have been associated with Chinese-speaking actors in the past.
Tunnelers
To further complicate detection and forensic tracing, TGR-STA-1030 incorporated tunneling utilities designed to relay traffic through intermediary VPS infrastructure. This layered routing approach masked the origin of command traffic and hindered incident response efforts.
- GOST (GO Simple Tunnel): Enables encrypted TCP/UDP forwarding across segmented environments.
- FRPS (Fast Reverse Proxy Server):Commonly used to expose internal services to external C2 servers.
- IOX: A cross-platform tunneling and proxy tool that supports covert data exfiltration channels.
By combining tunnelers with leased VPS relay nodes, the group effectively implemented multi-hop communication chains, significantly raising the complexity of attribution and infrastructure takedown efforts. This operational model aligns with long-dwell espionage objectives observed throughout the broader TGR-STA-1030 campaign.
ShadowGuard Rootkit: Advanced Linux Stealth Mechanism
A particularly notable component of TGR-STA-1030 cyber espionage activity is a Linux kernel rootkit dubbed ShadowGuard. This malware leverages Extended Berkeley Packet Filter (eBPF) technology to manipulate kernel behavior. ShadowGuard capabilities include:
- Concealing malicious processes from tools such as ps
- Intercepting system calls to hide directories and files named “swsecret”.
- Obscuring process metadata from user-space analysis
The use of eBPF-stealth mechanisms indicates a high level of Linux tradecraft that is not commonly seen elsewhere. (See Linux hosting)

Infrastructure Strategy and Long-Term Persistence
According to the findings, the group has been observed leasing its infrastructure from a legitimate VPS provider to host C2 servers. Additional relay servers are used to route traffic, forming multi-hop obfuscation paths.
The use of a multi-infrastructure strategy enabled the adversary to achieve persistence within the compromised environment for months. The adversary’s prolonged dwell time within the environment indicates that TGR-STA-1030 cyber espionage activities are not focused on rapid monetization. (Try 360monitoring)
Strategic Targeting and Geopolitical Implications
The targeting pattern shows a focus on nations involved in economic partnerships that are relevant to regional strategic interests. Ministries of finance, trade, and foreign affairs were repeatedly targeted, showing a focus on macroeconomic intelligence gathering. As Unit 42 reports:
“TGR-STA-1030 is an active threat to governments and critical infrastructure around the globe.”
The scope of this attack, the careful reconnaissance, and the persistence over time show that there is a long-term threat to national security. Although there was no zero-day exploit in this attack, the use of phishing, N-day exploitation, and advanced stealth technology shows that the attackers have reached a high level of maturity.
Frequently Asked Questions
What is TGR-STA-1030?
TGR-STA-1030 is a state-backed cyber espionage group identified by Palo Alto Networks Unit 42 that has targeted government and critical infrastructure entities worldwide.
How many organizations were compromised?
At least 70 government and infrastructure organizations across 37 countries were confirmed breached.
Did the group use zero-day exploits?
There is no evidence of zero-day exploitation; the group relied on phishing and unpatched N-day vulnerabilities.
What malware was used in the campaign?
The campaign utilized Diaoyu Loader, Cobalt Strike, multiple web shells, tunneling utilities, and a Linux rootkit known as ShadowGuard.
Why is this campaign significant?
Its global scale, long-term persistence, and targeting of sensitive government sectors indicate strategic intelligence objectives with potential geopolitical impact.
