
Protecting your website from DDoS attacks requires understanding how these attacks operate and preparing a multi-layered defense strategy. A DDoS attack overwhelms a server, service, or network by flooding it with traffic, often using compromised devices in a botnet. Without proper precautions, even short-lived attacks can lead to downtime, lost revenue, and reputational damage. Implementing prevention strategies ensures your website stays operational.
What is a Distributed Denial of Service (DDoS) Attack?
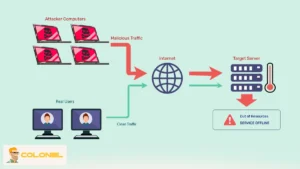
A DDoS attack is an attempt to make your website or network unavailable by sending excessive requests from multiple sources simultaneously. Attackers often leverage malware-infected devices to create botnets, which can target servers with immense traffic loads. The main goal is to exhaust system resources, causing slowdowns or complete outages. Understanding the nature of these attacks is the first step toward implementing effective protections.
Carnegie Mellon Software Engineering Institute (SEI) explains:
“A volumetric DDoS attack is like calling every pizza place in town and ordering dozens of pizzas to overwhelm a single customer. The result is chaos without actually breaking anything physically.”
How DDoS Attacks Work?
DDoS attacks can take various forms, but they all share a common mechanism: overloading network, application, or server resources. Attackers may exploit network protocols, application-layer vulnerabilities, or volumetric amplification techniques. A botnet often directs traffic to mimic legitimate users, making detection difficult. Recognizing the difference between normal traffic spikes and malicious activity is critical for implementing responsive security measures.

WordPress Web Hosting
Starting From $3.99/Monthly
Common Types of DDoS Attacks
Understanding attack types allows you to select appropriate mitigation strategies. The most common DDoS attacks include:
- Volumetric Attacks: These attacks consume bandwidth using amplification methods like UDP floods or ICMP floods. They aim to saturate the network, preventing normal traffic from passing through.
- Protocol Attacks: Targeting network protocol vulnerabilities, such as SYN floods, these attacks exhaust server or firewall resources, disrupting connection-handshake processes.
- Application-Layer Attacks: Layer 7 attacks overwhelm the server with seemingly legitimate requests, stressing the application rather than the network. These are complex because they appear as normal user activity.
According to Carnegie Mellon’s Software Engineering Institute, “A volumetric DDoS attack is like calling every pizza place in town and ordering dozens of pizzas to overwhelm a single customer. The result is chaos without actually breaking anything physically” (source).
Why Protecting Against DDoS Attacks Matters?
Preventing DDoS attacks is critical because they disrupt user access, reduce SEO performance, and can lead to financial loss. Beyond downtime, repeated attacks may damage your reputation and erode user trust.
Moreover, search engines increasingly factor in user experience metrics; a site prone to outages may see a decline in rankings. Therefore, DDoS prevention is not only a security measure but also an SEO and business continuity strategy.
Key Strategies to Protect Your Website from DDoS Attacks
To effectively protect your website from DDoS attacks, it’s essential to implement multiple complementary strategies. These strategies focus on reducing your exposure, detecting abnormal activity early, and mitigating attacks before they affect critical infrastructure. A layered approach ensures your network remains resilient and your services continue uninterrupted.
- Know Your Network Traffic: Establish a baseline for typical traffic patterns to distinguish between legitimate traffic spikes and malicious activity.
- Reduce Attack Surface: Limit open ports, unused services, and protocols to minimize potential attack vectors.
- Implement Real-Time Monitoring: Continuous network monitoring helps detect anomalies, allowing for a quick response to threats.


Cheap VPS Server
Starting From $2.99/Monthly
Step-by-Step Methods to Prevent DDoS Attacks
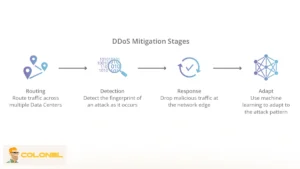
Preventing DDoS attacks requires a proactive, multi-layered approach. Simply relying on a firewall is insufficient because sophisticated attacks can mimic legitimate user traffic, making detection difficult. A robust strategy involves understanding your network, preparing response plans, and implementing tools that mitigate traffic surges and block malicious requests. By taking preemptive measures, you reduce the likelihood of service disruption and maintain user trust. To systematically protect your infrastructure, follow these key steps:
Create a Denial-of-Service Response Plan
When a DDoS attack occurs, organizations without a plan risk confusion, delayed response, and prolonged downtime. A well-prepared Denial-of-Service Response Plan ensures every team member knows exactly what steps to take. The goal is to minimize impact and restore normal operations as quickly as possible. To implement an effective plan:
- Develop a Systems Checklist – List all critical systems, servers, and services, including their dependencies. Knowing what to protect first can save valuable time during an attack.
- Identify and Train a Response Team – Assign dedicated personnel for IT, security, and communications. Regular drills and simulations improve response speed and reduce errors.
- Establish Escalation Paths – Clearly define how and when to escalate issues internally and externally, ensuring stakeholders receive timely alerts without overwhelming teams.
- Prepare Communication Plans – Draft pre-approved messages for employees, clients, and vendors. Transparent communication mitigates confusion and maintains trust during incidents.
- Include Mitigation Protocols – Detail steps for applying rate limits, activating CDN defenses, and engaging DDoS mitigation providers to quickly counteract ongoing attacks.
By predefining each element, your organization can respond methodically, reduce downtime, and ensure that technical and business teams act cohesively under pressure.
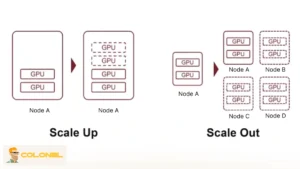
Scale Up Bandwidth and Infrastructure
Increasing bandwidth and distributing workloads is a strategic approach to absorb abnormal traffic surges caused by DDoS attacks. While it won’t stop malicious traffic, scaling buys time for defensive tools to act and prevents immediate service outages. From an analytical perspective:
| Advantages | Limitations |
| Accommodates sudden traffic spikes | Cannot fully mitigate sophisticated attacks |
| Reduces bottlenecks by distributing servers across multiple locations | Requires ongoing infrastructure investment |
| Provides redundancy if one node becomes overloaded | Needs continuous monitoring |
Organizations should evaluate network usage patterns, forecast peak loads, and integrate scalable cloud resources. This layered approach ensures that when an attack occurs, critical systems remain operational long enough for mitigation strategies to neutralize threats.

Windows VPS Hosting
Remote Access & Full Admin
Use Content Delivery Networks (CDNs) and Caching
Content Delivery Networks (CDNs) and caching are not just performance optimizations—they are critical defensive mechanisms against DDoS attacks. CDNs replicate your content across geographically distributed servers, while caching stores frequently accessed data closer to users. The deeper impact is twofold:
- Load Distribution: Traffic requests are spread over multiple nodes, reducing the strain on origin servers. Even if an attacker floods one node, other nodes continue servicing legitimate users.
- Volumetric Attack Resistance: By handling repetitive requests locally (via cache), CDNs limit the volume of traffic that reaches the main infrastructure. This reduces bandwidth consumption and helps maintain uptime.
Conceptually, CDNs and caching transform your network from a single point of failure into a resilient, layered system. For organizations hosting critical web services, integrating CDNs is both a security and performance necessity.
Implement Rate Limiting
Rate limiting is a proactive measure that prevents individual IP addresses or user sessions from overwhelming your servers. This approach is particularly effective against botnets, which are commonly employed in DDoS attacks. Apply rate limiting effectively through:
- Define Request Thresholds: Set maximum requests per IP or session within defined time windows.
- Differentiate User Types: Allow higher limits for trusted or authenticated users while restricting anonymous traffic to prevent disruption.
- Monitor and Adjust: Regularly review traffic patterns to refine thresholds, ensuring legitimate users aren’t blocked while mitigating attack traffic.
Rate limiting acts as a traffic filter at the application or network level. Real-world examples show that it can neutralize automated attacks that attempt to flood endpoints without affecting standard user activity. When combined with logging and alert systems, it enables early detection and rapid response.
Deploy Always-On DDoS Mitigation Tools
Cloud-based, always-on DDoS mitigation platforms provide continuous traffic monitoring, automatic threat filtering, and global traffic dispersion. Services like Cloudflare use Anycast networks to distribute incoming requests, absorbing even large-scale attacks before they reach your servers. The key pros and cons of deploying always-on DDoS mitigation tools are:
| Advantages | Limitations |
| Real-time threat response blocks malicious traffic instantly | Cannot prevent all types of highly sophisticated, targeted attacks |
| Scalable protection adapts automatically to traffic spikes | Requires subscription to cloud-based mitigation services |
| Integrated security features (WAF, rate limiting, geo-filtering) provide layered defense | Dependent on provider reliability and network coverage |
| Reduces risk of extended outages and preserves access for legitimate users | May introduce slight latency due to traffic inspection and filtering |
| Proactive security posture allows organizations to respond without manual intervention | Ongoing management and configuration updates are necessary |
By adopting always-on mitigation, organizations gain a proactive security posture, reducing the risk of extended outages and preserving access for legitimate users during attacks. The combination of automation, global infrastructure, and policy-based filtering makes it one of the most reliable defenses against modern DDoS threats.
Recommended Tools and Services
Using the right tools is critical to prevent DDoS attacks effectively. Each tool addresses specific layers of traffic and attack vectors:
- Web Application Firewalls (WAFs): WAFs inspect incoming requests to block malicious traffic targeting application vulnerabilities. Advanced WAFs offer customizable rulesets and adaptive policies to respond to evolving attack patterns.
- Intrusion Prevention Systems (IPS): IPS solutions detect anomalies in protocol behavior, such as SYN floods or state-exhaustion attacks, and automatically block suspicious activity before it affects systems.
- Cloud-Based DDoS Mitigation: Cloud providers use global networks to diffuse traffic, balance loads, and maintain service availability during volumetric attacks. Scalability is key for managing high-volume threats.
- SecurityScorecard: This platform continuously monitors external attack surfaces, identifies vulnerabilities, and analyzes abnormal traffic patterns to prevent escalation into full-scale DDoS events (source).
Combining these technologies ensures a multi-layered defense that addresses network-level, protocol-level, and application-level threats.
Recognizing the Signs of a DDoS Attack
Early detection is crucial. DDoS attacks often blend malicious traffic with legitimate users, so identifying unusual patterns quickly is essential. Some common indicators include:
- Unexpected website slowdowns or outages
- Spike in traffic from specific IP addresses or regions
- Unusually high demand on a single page or endpoint
- Intermittent connectivity or service crashes
Continuous monitoring of baseline traffic patterns allows IT teams to detect deviations. Real-time analytics, integrated with rate limiting and geo-blocking, help proactively counter attacks while preserving access for legitimate users.
Outsourcing DDoS Protection
For many organizations, outsourcing is an effective strategy. DDoS-as-a-Service providers specialize in scaling resources, deploying mitigation strategies during attacks, and restoring service quickly. Outsourcing can include:
- Immediate scaling of infrastructure to absorb traffic spikes
- Automatic filtering and blocking of malicious requests
- Post-attack reporting and analysis to improve future defenses
This approach reduces operational overhead while ensuring rapid response to high-intensity attacks.

Best Practices for Comprehensive DDoS Protection
To effectively protect your website from DDoS attacks, it is recommended to implement multiple layers of defense simultaneously:
- Monitor and understand normal traffic patterns to detect anomalies.
- Reduce the attack surface by disabling unused ports, protocols, and services.
- Maintain and regularly update a DDoS response plan with trained staff.
- Utilize CDNs and caching to reduce server load.
- Implement rate limiting for high-traffic endpoints.
- Deploy WAFs, IPS, and cloud-based mitigation tools.
- Continuously monitor traffic and outsource protection when necessary.
This combination ensures resilience, maintains uptime, and protects against both small-scale and sophisticated attacks.
A proactive, layered defense strategy that combines monitoring, mitigation tools, and response planning ensures websites remain operational even under high-volume DDoS attacks. Organizations that integrate these measures maintain uptime, protect user trust, and enhance overall cybersecurity resilience.
Frequently Asked Questions (FAQs)
How can I quickly identify a DDoS attack?
Sudden traffic spikes, unusual slowdowns, and repeated system crashes can signal a DDoS attack. Regular monitoring of traffic patterns is key for early detection.
Can a firewall alone stop a DDoS attack?
No. Firewalls handle basic filtering but are insufficient for complex attacks that mimic legitimate traffic. A layered approach is essential.
What is a DDoS botnet?
A botnet is a network of compromised devices controlled by attackers to generate malicious traffic aimed at overwhelming a target.
Is cloud hosting safer against DDoS attacks?
Cloud hosting provides higher bandwidth and integrated mitigation, which can absorb traffic spikes, but does not fully eliminate DDoS risks.
How often should I update a DDoS response plan?
It should be reviewed quarterly or after any major infrastructure changes to ensure effectiveness during an attack.
