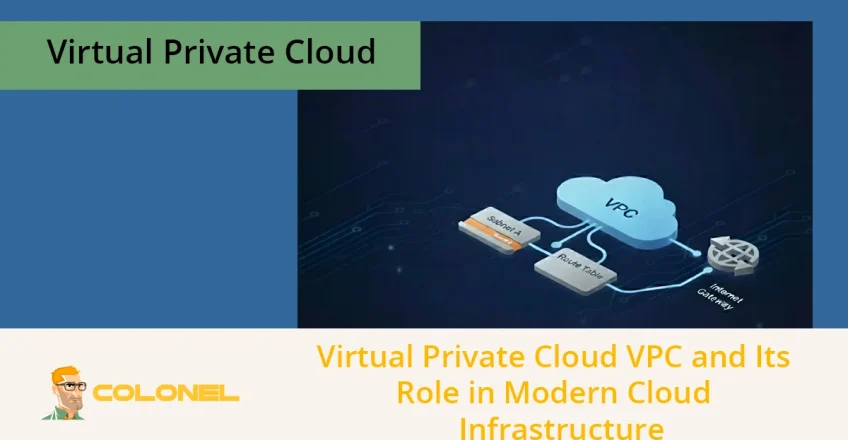
A virtual private cloud (VPC) is a logically isolated network environment that runs within a public cloud provider’s infrastructure, providing organizations with full control over networking, security, and resource placement. Unlike the open structure of the public cloud, a VPC allows you to design a private, enterprise-grade network while still benefiting from cloud scalability and managed infrastructure.
In a modern cloud strategy, a VPC is not an optional feature. It is the baseline for building compliant, scalable, and predictable infrastructure in the cloud.
What Is a Virtual Private Cloud (VPC)?
A virtual private cloud (VPC) is a private network space within a public cloud where only your organization’s resources operate, fully isolated from other cloud tenants. This isolation is logical rather than physical, but from a security and control standpoint, it closely mirrors dedicated infrastructure. Administrators decide:
- How IP addressing works
- How traffic moves between subnets
- Which systems can communicate
- Which resources are exposed to the internet
This level of governance makes VPCs suitable for enterprise workloads that cannot tolerate shared, unmanaged network environments.
For machine learning, analytics, and regulated industries, a VPC ensures that compute resources remain predictable and that data flows are fully auditable. In practice, it delivers the familiarity of traditional networking with the automation and elasticity of the cloud.


WordPress Web Hosting
Starting From $3.99/Monthly
How a Virtual Private Cloud Works
A virtual private cloud operates by creating a private, software-defined network on top of a cloud provider’s shared infrastructure. While the underlying hardware is shared, networking boundaries ensure that traffic never crosses into another tenant’s environment.
At a technical level, the virtual private cloud relies on private IP addressing, virtual routing tables, and controlled gateways. Resources inside the VPC communicate using internal addresses, while external access is tightly regulated through gateways, firewalls, and routing rules.
This architecture allows organizations to deploy cloud workloads without exposing internal systems to the public internet. Even when internet access is required, it is explicitly configured and monitored, ensuring that security posture remains intact.
Why Virtual Private Clouds Are the Foundation of Modern Cloud Architecture
Virtual private clouds have become the standard starting point for cloud adoption because they solve the core tension between flexibility and control. Organizations want cloud speed without sacrificing security, compliance, or architectural clarity.
A virtual private cloud (VPC) enables teams to replicate familiar enterprise network designs while eliminating physical infrastructure constraints. Subnets replace physical VLANs, routing tables replace hardware routers, and security policies are enforced consistently across dynamic environments.
This approach is particularly valuable for organizations running complex systems such as distributed applications, multi-tier platforms, or machine learning pipelines. The VPC ensures that growth does not introduce chaos and that scaling remains structured rather than improvised.

Cheap VPS Server
Starting From $2.99/Monthly
Key Benefits of a Virtual Private Cloud
The advantages of a virtual private cloud appear most clearly in day-to-day operations. Rather than being theoretical, these benefits directly affect security posture, deployment speed, and long-term scalability. According to Google Cloud documentation:
“VPC networks provide logically isolated virtual networks for resources in Google Cloud.”
Security Through Logical Isolation
A virtual private cloud improves security by isolating your workloads from other tenants in the public cloud. Traffic is restricted by default, and access rules are explicitly defined rather than implied.
This design significantly reduces the attack surface. Sensitive workloads such as financial systems, healthcare data, or proprietary machine learning models remain shielded from external exposure. Logging and monitoring tools further enhance visibility, making audits and compliance checks easier to perform. According to Amazon:
“Netflix highlights the operational value of this approach by using VPC Flow Logs to analyze massive volumes of network traffic in near real time, allowing security teams to detect anomalies before they escalate.”


Windows VPS Hosting
Remote Access & Full Admin
Flexibility in Network Design
A virtual private cloud (VPC) is not a fixed template. It allows teams to design networks that reflect real operational needs rather than forcing workloads into generic structures.
Development, staging, and production environments can be isolated using separate subnets. Routing rules can enforce strict boundaries between training and inference systems in ML pipelines. As requirements change, the network adapts without downtime or hardware changes.
This flexibility supports experimentation without compromising stability, which is essential for organizations operating at scale.
Elastic Scalability Without Redesign
Scalability is one of the most practical benefits of a virtual private cloud. As demand grows, new resources can be added to the existing network without altering its structure.
Whether scaling web services or adding hundreds of GPU nodes for training large models, routing rules and security policies remain intact. This eliminates the need for repeated architectural redesigns, a common limitation of on-premises data centers.
Virtual Private Cloud vs On-Premises Data Centers
A virtual private cloud (VPC) often replaces or complements traditional on-premises infrastructure, but the two models differ significantly in execution.
On-premises environments rely on physical isolation and hardware ownership. While this offers direct control, it comes with high upfront costs, long deployment cycles, and ongoing maintenance burdens. Scaling requires procurement, installation, and manual configuration.
By contrast, a virtual private cloud delivers similar isolation through logical boundaries. Security, routing, and segmentation are handled via provider tools and APIs. The result is faster deployment, easier scaling, and lower operational overhead, without sacrificing governance or compliance.
Core Components of a Virtual Private Cloud
A virtual private cloud functions as a complete networking environment because it is built from several tightly integrated components. Each element plays a specific role in how the VPC operates.
CIDR Blocks and IP Addressing
CIDR blocks define the IP address space available within a VPC and form the foundation of all networking decisions. Choosing the right CIDR range is critical, especially for environments expected to grow.
Poor planning can lead to address exhaustion or conflicts with on-premises networks in hybrid setups. For machine learning teams, where distributed training may involve hundreds of nodes, a well-sized CIDR block prevents future re-architecture.
Subnets and Network Segmentation
Subnets divide the VPC into logical segments that isolate workloads based on function or exposure level. Public-facing services typically reside in public subnets, while internal systems operate in private ones.
This separation improves both security and manageability. For example, inference APIs may be internet-accessible, while training clusters and data stores remain completely private. Clear segmentation also simplifies troubleshooting and compliance audits.
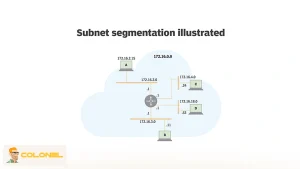
Routing Tables and Traffic Flow Control
Routing tables determine how traffic moves inside and outside the virtual private cloud. Each subnet is associated with a routing table that defines which destinations are reachable.
Routing controls connectivity, not security. Removing an internet route can fully isolate a subnet, while security groups handle port-level access. This distinction allows precise control over data movement without overcomplicating firewall rules.
Internet Gateways and NAT
An Internet Gateway is the component that enables resources inside a virtual private cloud (VPC) to communicate with the public internet under strict conditions. It does not automatically expose all resources; only instances explicitly assigned public IP addresses and proper routing rules can use it.
In practice, Internet Gateways are typically attached to public subnets hosting web applications or inference APIs. Private subnets, such as those used for databases or machine learning training clusters, remain inaccessible from the internet unless paired with controlled outbound mechanisms.
For outbound-only access, Network Address Translation (NAT) gateways are commonly used. A NAT gateway allows private resources to download updates or external dependencies without accepting inbound connections. This pattern is widely adopted to maintain security boundaries while preserving operational flexibility.
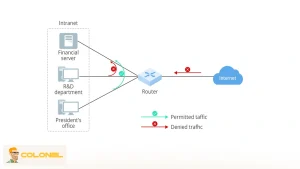
Security Groups and Network ACLs
Security in a virtual private cloud (VPC) relies on multiple enforcement layers rather than a single firewall. The two most important mechanisms are security groups and network access control lists (NACLs), each serving a distinct role.
Security Groups as Stateful Firewalls
Security groups act as stateful firewalls attached directly to instances or network interfaces. They define which inbound and outbound traffic is allowed, and any response traffic is automatically permitted. This makes them ideal for fine-grained control over application-level access.
In real-world architectures, security groups often restrict databases so that only application servers or inference nodes can connect. As environments scale, newly added instances inherit these rules immediately, maintaining consistency without manual intervention.
Network ACLs for Subnet-Level Enforcement
Network ACLs operate at the subnet level and are stateless, meaning inbound and outbound rules are evaluated independently. Unlike security groups, ACLs support both allow and deny rules, making them suitable as a defensive safety layer.
Organizations handling sensitive data frequently use ACLs to block entire traffic classes, such as inbound internet access to private subnets. This ensures that even misconfigured instances remain protected by default.
Load Balancers in a Virtual Private Cloud
Load balancers distribute incoming traffic across multiple instances to ensure availability and performance. Inside a virtual private cloud (VPC), they also act as controlled entry points into private infrastructure.
Application-level load balancers handle HTTP and HTTPS traffic, terminate TLS connections, and route requests based on paths or hostnames. This is particularly valuable for microservices and machine learning inference endpoints, where traffic patterns can fluctuate rapidly.
By continuously monitoring instance health, load balancers remove unhealthy nodes from rotation automatically. This prevents service disruption and allows teams to deploy updates or scale resources without downtime.
VPN and Hybrid Connectivity
A Virtual Private Network (VPN) connects a virtual private cloud (VPC) to on-premises environments through encrypted tunnels. This integration allows cloud resources to behave as an extension of internal corporate networks.
For enterprises transitioning gradually to the cloud, VPNs provide continuity. Applications can access legacy systems securely, and data does not need to be duplicated or exposed publicly. More advanced setups use dedicated connections such as Direct Connect or Interconnect for higher throughput and lower latency.
Hybrid architectures are especially common in machine learning workflows, where training may occur in the cloud while datasets remain on-premises due to compliance or cost constraints.
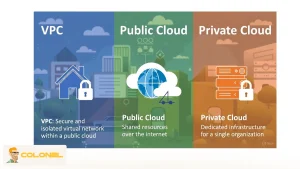
VPC vs Public Cloud vs Private Cloud
A Virtual Private Cloud (VPC) sits between public and private cloud models by offering strong logical isolation while still benefiting from the scalability and managed infrastructure of public cloud platforms. The key differences between VPC, Public Cloud, and Private Cloud are outlined clearly in the table below.
| Aspect | Virtual Private Cloud (VPC) | Public Cloud | Private Cloud |
| Isolation level | Logical isolation within a shared cloud infrastructure, enforced through networking and access controls | Minimal isolation, resources are shared among multiple tenants | Full physical isolation with dedicated hardware |
| Security control | High control over network rules, access policies, and traffic flow | Limited control, security largely managed by the provider | Maximum control over security, compliance, and data handling |
| Scalability | Highly scalable with on-demand resource expansion inside a private network | Extremely scalable with instant access to shared resources | Scaling is slow and depends on hardware procurement |
| Operational overhead | Moderate, infrastructure is managed by the provider while configuration remains user-controlled | Low, most operations are abstracted by the provider | High, all maintenance, upgrades, and monitoring are handled in-house |
| Cost structure | Pay-as-you-go with no upfront hardware investment | Lowest entry cost, usage-based pricing | High upfront and ongoing costs for hardware and staffing |
| Network customization | Custom IP ranges, subnets, routing tables, and security policies | Very limited network customization | Full customization at physical and network layers |
| Compliance suitability | Well suited for regulated workloads requiring isolation and auditability | Often insufficient for strict compliance requirements | Ideal for highly regulated industries |
| Typical use cases | Enterprise applications, regulated workloads, ML and AI systems | General web apps, testing, low-risk workloads | Finance, healthcare, government, sensitive data systems |
How VPCs Support Machine Learning and AI Workloads
Virtual private clouds are particularly well suited for machine learning environments because they combine predictability with scale. Training large models often requires hundreds of GPU nodes operating in parallel, and uncontrolled networking introduces unacceptable risk.
Within a virtual private cloud (VPC), teams isolate training, inference, and data preparation into separate subnets. Routing rules ensure that data flows only where intended, while security groups prevent unauthorized access to models or datasets.
This structure supports reproducibility, which is essential for ML experimentation. Engineers can recreate environments consistently, track data movement, and audit access without relying on external network controls.
Getting Started with Virtual Private Cloud in Nebius
Nebius integrates virtual private cloud (VPC) functionality directly into its AI Cloud platform, allowing compute, storage, and networking to operate within a single isolated environment. GPU instances, Kubernetes clusters, and storage services all reside inside the same private network.
Setup focuses on defining subnets, routing rules, and access policies rather than low-level infrastructure. As workloads expand, new nodes join the existing VPC automatically while maintaining isolation and security controls.
Nebius documentation provides practical guidance for building GPU training clusters and production inference systems within a virtual private cloud network.
Why Virtual Private Clouds Have Become the Default Cloud Foundation
A virtual private cloud (VPC) is not just a networking feature but the structural backbone of modern cloud environments. It delivers isolation without rigidity, control without hardware constraints, and scalability without architectural chaos.
As organizations adopt cloud-native and AI-driven systems, predictable networking and security are no longer optional. VPCs provide the framework to grow confidently while maintaining governance, compliance, and operational clarity.
For businesses that require both agility and control, the virtual private cloud remains the most practical and future-proof foundation for cloud infrastructure.
Frequently Asked Questions About Virtual Private Cloud (VPC)
What is the main purpose of a virtual private cloud (VPC)?
The main purpose of a virtual private cloud is to provide a secure, isolated network environment inside a public cloud while retaining full control over routing, access, and resource placement.
Is a VPC more secure than a public cloud?
Yes, a VPC is more secure because workloads are logically isolated and access rules are explicitly defined rather than shared across tenants.
Can a VPC replace an on-premises data center?
In many cases, a VPC can replace on-premises infrastructure by delivering comparable control with lower operational overhead and faster scalability.
Does a virtual private cloud support hybrid architectures?
A virtual private cloud supports hybrid setups through VPNs and dedicated connections, enabling secure integration with on-premises systems.
Is a VPC suitable for machine learning workloads?
Yes, VPCs are ideal for machine learning because they offer predictable networking, strict isolation, and seamless scaling for large training clusters.
