
What Is TLS? Transport Layer Security, or TLS, is an essential protocol that provides confidentiality, integrity, and authentication of data exchanged over the internet. In this practical guide to secure web data, the technical aspects of Transport Layer Security are discussed, and the way encryption, trust through certificates, and secure handshake ensure that there is no interception, data alteration, or man-in-the-middle attacks. Knowing What Is TLS? and its technical aspects of implementation in web applications, APIs, and server infrastructure is critical for the creation of secure, compliant, and scalable digital solutions in the current threat-centric online ecosystem.
What Is TLS and Why It Matters
Transport Layer Security (TLS) is one of the most essential components of contemporary internet security. Every time a user visits a website, enters credentials, makes an online payment, or communicates with an API, TLS operates in the background to safeguard confidential information from being intercepted and tampered with. It is important for security professionals, developers, system administrators, and organizations that require secure online communication to comprehend the significance of What Is TLS.
In the current threat environment, unencrypted traffic poses an invitation to attackers. Confidential information that travels over the internet without encryption can be intercepted, modified, or spoofed by attackers using simple tools. TLS mitigates these threats by offering encryption, authentication, and integrity checks to ensure that the information arrives at its destination securely and intact.
Definition of Transport Layer Security (TLS)
Transport Layer Security (TLS) is a protocol for secure computer network data communication. TLS is used to encrypt and decrypt data in computer networks. TLS works by encrypting information before sending it and decrypting it when it reaches the destination. TLS works between the application layer and the transport layer in computer networks. TLS encrypts information before sending it and decrypts it when it reaches the destination.
Transport Layer Security (TLS) is used to secure computer networks from unauthorized access and forgery. TLS has three main components: symmetric encryption, asymmetric encryption, and hashing. TLS uses these three components to secure computer networks.

WordPress Web Hosting
Starting From $3.99/Monthly
When computer professionals ask, “What is TLS?” The best and most accurate way to define TLS is to tell them that TLS is not an encryption method but rather an amalgamation of different encryption techniques.
TLS vs SSL: Key Differences and Evolution
Both TLS and SSL are often mentioned together, creating confusion. However, SSL was the original protocol developed by Netscape in the 1990s, but it had several design flaws and vulnerabilities. Then came TLS as its successor, enhancing security and standardization.
While many people are still using the term “SSL,” the truth is that modern systems are actually using TLS. SSL versions (SSL 2.0 and SSL 3.0) are now deemed insecure and have been officially deprecated. TLS not only resolves the cryptographic flaws in SSL but also provides better algorithms, handshakes, and extensibility.
It is also important to understand What Is TLS in the context that the SSL protocol is obsolete, and any system that claims to be using SSL is either misconfigured or using outdated terminology.
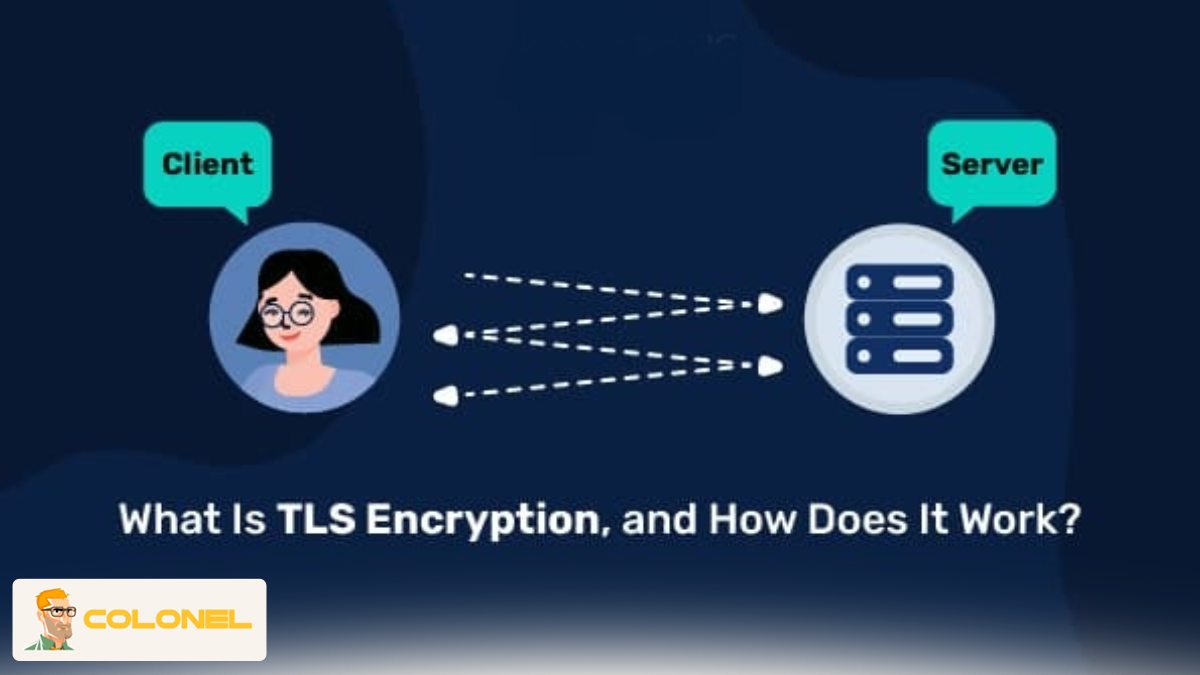
How TLS Works
TLS works by creating a secure and encrypted channel for both the client and server before data is transmitted. This ensures that both parties can communicate in a secure environment even when using an insecure network.

Cheap VPS Server
Starting From $2.99/Monthly
The TLS Handshake Process
The TLS handshake is the initial process in which both the client and server negotiate their security settings. During this process, both parties agree on which version of the protocol to use, which algorithms to implement, which identities to authenticate, and which keys to use for shared encryption.
The handshake process starts when the client sends a “ClientHello” message with information about which version of TLS it can support and which algorithms it can implement. Once this is done, the server responds with a “ServerHello,” which contains information about which version it can support and its digital certificate.
For someone who is learning about “What Is TLS,” this is an important part of understanding the protocol.
Encryption, Authentication, and Data Integrity
The three main security services offered by TLS are:
- Encryption ensures confidentiality, as data is not readable when intercepted by an unauthorized party.
- Authentication ensures that both communicating parties are who they claim to be, usually through digital certificates.
- Data Integrity ensures that data has not been tampered with in transit.
All three services combined ensure that various attack scenarios such as sniffing, spoofing, and man-in-the-middle are mitigated. Without TLS, data can easily be intercepted and tampered with by an attacker.
The Role of Public Key Infrastructure (PKI)
The Public Key Infrastructure (PKI) is an essential part of TLS. PKI is a set of policies and procedures used for issuing, managing, and validating digital certificates. PKI uses trusted Certificate Authorities (CAs) to authenticate the identity of both servers and clients.

Windows VPS Hosting
Remote Access & Full Admin
When a server sends a certificate to a client as part of the TLS handshake, the client validates it with a trusted list of Certificate Authorities. This is essentially an answer to one of the most important questions posed by What Is TLS: How is trust established between two unknown parties?
TLS Versions and Evolution of Protocols
The TLS protocol has undergone a lot of evolution since its inception. Each new version of the protocol has brought improvements to the security, performance, and resistance to attacks.
Summary of TLS 1.0, 1.1, 1.2, and 1.3 Versions
The initial versions of the TLS protocol (1.0 and 1.1) brought in many essential security elements but also carried some vulnerabilities from the SSL protocol. The version 1.2 of the protocol brought in a significant improvement with the support for new cryptographic algorithms and flexible cipher suite negotiation.
The evolution of the different versions of the TLS protocol is summarized in the table below:
| TLS Version | Release Year | Security Status | Key Characteristics |
| TLS 1.0 | 1999 | Deprecated | Based on SSL 3.0, weak algorithms |
| TLS 1.1 | 2006 | Deprecated | Improved IV handling |
| TLS 1.2 | 2008 | Widely used | Strong ciphers, SHA-256 support |
| TLS 1.3 | 2018 | Recommended | Faster handshakes, improved security |
Understanding What Is TLS today means focusing on TLS 1.2 and especially TLS 1.3, as older versions are no longer considered secure.
Why TLS 1.3 Is More Secure and Faster
TLS 1.3 is a more secure and faster protocol compared to its predecessors. This is because it eliminates certain insecure features in earlier protocols and also simplifies the protocol handshake. Furthermore, it enforces forward secrecy by default and also eliminates weak cipher suites.
As Cloudflare, a leading web security provider, puts it:
“TLS 1.3 is faster and more secure than its predecessors, removing legacy cryptography and reducing handshake latency.”
The above quote emphasizes the importance of using more advanced infrastructure with TLS 1.3.
Certificates and Trust in TLS
Digital certificates are the foundation for trust in TLS-based communication. The client would have no way to verify the identity of the server without digital certificates.
Digital Certificates and Certificate Authorities (CAs)
A digital certificate is an association between an entity’s identity and its corresponding public key. The certificate is issued by Certificate Authorities.
Certificate Authorities are trusted third parties. The Certificate Authorities are stored in the client’s web browser or the client’s operating system. When the client connects to the server, the client checks the certificate issued by the Certificate Authority. The Certificate Authority’s digital signature is verified by the client. The certificate’s validity is also verified by the client. The client is assured that it is connecting to the intended server.
Understanding What Is TLS requires an understanding of the role played by digital certificates in the authentication process.
How Certificate Validation Works
Certificate validation occurs by verifying the digital signature, the expiration date, the domain name, and the revocation status. If any of these conditions are not met, the TLS connection is considered untrusted.
This validation process ensures that an attacker does not impersonate the identity of the server using a forged certificate.

Common Certificate Errors and Misconfigurations
It is important to understand that, before delving into common certificate errors, certificate misconfigurations are one of the most common reasons that can lead to failures with TLS connections in production environments.
- Expired certificates due to a lack of renewal automation
- Domain name issues and/or missing SANs
- Incomplete certificate chains
- Self-signed certificates in public services
These errors can result in browser warnings, failed connections, and decreased trust with the user.
TLS Cipher Suites Explained
Cipher suites specify what particular encryption methods will be employed during a given TLS session. Using robust cipher suites for secure data transport is vital.
Symmetric vs. Asymmetric Encryption
In TLS, symmetric encryption methods are employed for data transport after a secure handshake using asymmetric encryption. Using symmetric encryption for data transport provides efficiency.
Key Exchange Algorithms
Key exchange methods specify how session keys will be generated. Current best practices for key exchange methods involve using Elliptic Curve Diffie-Hellman for key exchange.
Hash Functions and Message Authentication Codes (MAC)
Hash functions and MACs ensure data integrity by detecting unauthorized changes. They generate fixed-length digests that are verified by the receiving party.

Implementing TLS on Web Servers
Proper TLS implementation requires careful configuration and ongoing maintenance.
Enabling TLS on Apache, Nginx, and IIS
Most modern web servers support TLS out of the box. Administrators must install certificates, enable HTTPS, and configure protocol versions and cipher suites.
Configuring Strong Cipher Suites
Before listing best practices, it is important to understand that default configurations may not always provide optimal security.
- Prefer TLS 1.3 and TLS 1.2 only
- Disable weak ciphers such as RC4 and 3DES
- Use modern AEAD ciphers like AES-GCM
These steps significantly improve TLS security posture.
Enforcing HTTPS and HSTS
HTTP Strict Transport Security (HSTS) ensures that browsers always connect via HTTPS, preventing downgrade attacks and protocol stripping.
TLS Security Best Practices
TLS security best practices are essential for maintaining long-term protection against evolving cyber threats. While TLS itself is a robust protocol, its effectiveness heavily depends on correct configuration, continuous maintenance, and adherence to modern security standards. Misconfigured TLS settings can silently expose sensitive data, even when encryption is technically enabled. Organizations must therefore treat TLS as an ongoing security process rather than a one-time setup.
A well-maintained TLS implementation reduces attack surface, ensures compliance with security regulations, and preserves user trust. Regular reviews, updates, and monitoring are critical to keeping TLS deployments resilient in production environments.
!!!
If you are looking to apply TLS security in real-world, high-risk environments, it is worth exploring Private AI Hosting Designed for Business Security. This article explains how private hosting infrastructures leverage encryption, isolated resources, and strict access controls to protect sensitive AI workloads and business data. Reading it will help you understand how TLS fits into a broader security strategy designed for enterprises that require maximum data confidentiality and compliance.
Disabling Legacy Protocols and Weak Ciphers
Legacy TLS and SSL protocols significantly increase security risk because they rely on outdated cryptographic mechanisms that are vulnerable to modern attacks. Protocols such as SSL 2.0, SSL 3.0, TLS 1.0, and TLS 1.1 lack protections against known vulnerabilities like BEAST, POODLE, and downgrade attacks.
Disabling weak cipher suites is equally important. Algorithms such as RC4, DES, and 3DES are no longer considered secure and should never be used in production systems. Organizations should enforce the use of strong, modern cipher suites that support authenticated encryption, such as AES-GCM or ChaCha20-Poly1305.
Regular security audits and automated configuration scans help identify outdated protocol support and ensure that only approved cryptographic standards are enabled across servers and services.

Certificate Rotation and Renewal
Digital certificates have a finite lifespan, and expired certificates are one of the most common causes of TLS-related outages. Manual certificate management increases the risk of human error, forgotten renewals, and unexpected downtime.
Automated certificate rotation and renewal provide a reliable solution to this problem. Using ACME-based tools such as Certbot allows systems to automatically request, install, and renew certificates without manual intervention. Automation not only prevents service disruptions but also enforces shorter certificate lifetimes, which reduces the impact of key compromise.
In large environments, centralized certificate management ensures consistency across services, simplifies auditing, and supports rapid revocation if a private key is compromised.
Monitoring and Logging TLS Connections
Monitoring and logging TLS activity is critical for detecting security issues that may otherwise go unnoticed. TLS logs can reveal failed handshakes, expired certificates, unsupported protocol attempts, and suspicious connection patterns.
By analyzing TLS-related logs, security teams can identify potential attacks, misconfigurations, or unauthorized access attempts early. Integration with centralized logging and Security Information and Event Management (SIEM) systems enables correlation between TLS events and broader security signals.
Effective monitoring transforms TLS from a passive security mechanism into an active source of visibility and threat detection.
Common TLS Attacks and Mitigation
Despite its strong cryptographic foundation, TLS can still be compromised through implementation flaws, configuration errors, or outdated components. Most successful TLS attacks do not break encryption directly; instead, they exploit weaknesses in how TLS is deployed or enforced.
Understanding common attack techniques helps organizations design effective mitigation strategies and avoid repeating known mistakes.
Man-in-the-Middle (MITM) Attacks
Man-in-the-middle attacks occur when an attacker intercepts communication between a client and server, attempting to impersonate one or both parties. This can happen through compromised networks, malicious Wi-Fi hotspots, or forged certificates.
Proper certificate validation is the primary defense against MITM attacks. Clients must verify certificate chains, domain names, and trust anchors before establishing TLS connections. Enabling HTTP Strict Transport Security (HSTS) further strengthens protection by preventing browsers from accepting unencrypted or downgraded connections.
Certificate pinning, where appropriate, adds an additional layer of defense by restricting which certificates are considered valid for a specific service.
Downgrade and Replay Attacks
Downgrade attacks attempt to force a connection to use weaker protocol versions or cipher suites that are easier to exploit. Attackers manipulate handshake messages to trick systems into falling back to insecure configurations.
Replay attacks involve capturing encrypted traffic and replaying it later to perform unauthorized actions. These attacks are especially dangerous for authentication and transactional systems.
TLS 1.3 mitigates many of these risks by eliminating protocol downgrade paths, enforcing forward secrecy, and introducing built-in protections against replay attacks. Disabling legacy protocol support and enforcing strict version negotiation further reduces exposure.
Protecting Against Misconfiguration Risks
Misconfiguration remains one of the most significant threats to TLS security. Even strong cryptographic protocols can fail if incorrectly implemented. Common mistakes include incomplete certificate chains, inconsistent TLS settings across services, and exposing management interfaces without proper encryption.
Regular configuration reviews, automated compliance checks, and infrastructure-as-code practices help reduce human error. Testing TLS configurations using automated scanners ensures that changes do not introduce new vulnerabilities.
TLS Performance Considerations
While TLS provides essential security, it also introduces computational overhead. Modern TLS implementations are designed to minimize performance impact, but improper configuration can still lead to increased latency and resource usage.
Balancing security and performance is especially important for high-traffic websites, APIs, and real-time applications.
TLS Handshake Optimization
The TLS handshake is the most resource-intensive part of establishing a secure connection. Optimizing this process reduces connection latency and improves user experience.
Techniques such as enabling TLS 1.3, using efficient key exchange algorithms, and leveraging hardware acceleration significantly reduce handshake overhead. Proper server tuning ensures that secure connections scale efficiently under load.
Session Resumption and 0-RTT
Session resumption allows clients to reuse cryptographic parameters from previous connections, eliminating the need for a full handshake. This significantly reduces latency for returning users.
TLS 1.3 introduces 0-RTT (Zero Round Trip Time), which allows data to be sent immediately during connection setup. While 0-RTT improves performance, it must be used carefully due to replay risks and should be limited to idempotent requests.
Impact of TLS on Web Performance
With modern CPUs, optimized cryptographic libraries, and efficient TLS versions, the performance cost of encryption is minimal. In most cases, network latency outweighs TLS processing time.
As a result, TLS encryption is now considered a baseline requirement rather than a performance trade-off, even for large-scale systems.
When and Where TLS Should Be Used
In modern digital environments, TLS is not optional—it is a foundational security requirement. Any system that transmits data over a network should use TLS to protect confidentiality and integrity.
TLS for Websites, APIs, and Microservices
Public websites use TLS to protect user data, authentication credentials, and payment information. APIs rely on TLS to secure machine-to-machine communication and prevent data leakage.
In microservices architectures, TLS enables secure service-to-service communication, supporting zero-trust security models where every request must be authenticated and encrypted, even within internal networks.
TLS in Cloud and Containerized Environments
Cloud-native platforms use TLS extensively for ingress controllers, service meshes, and internal networking. Container orchestration systems rely on TLS for secure control-plane communication and secret management.
Understanding What Is TLS in these environments highlights its role as a universal security layer that protects dynamic, distributed systems at scale.
Conclusion
TLS is no longer a luxury or optional enhancement—it is a fundamental requirement for secure digital communication. From encrypting web traffic and protecting APIs to securing cloud-native architectures, TLS plays a central role in modern cybersecurity. By understanding What Is TLS, how it works, how it has evolved, and how to implement it correctly, organizations can significantly reduce risk, improve trust, and meet security and compliance expectations. Proper configuration, regular maintenance, and adoption of modern standards such as TLS 1.3 ensure that TLS continues to protect data effectively in an increasingly hostile online environment.
