Docker & Kubernetes container security is the structured practice of protecting container images, orchestration layers, and runtime environments from vulnerabilities, misconfigurations, and active threats across the entire container lifecycle. As organizations increasingly rely on containers for scalable cloud-native applications, understanding Docker & Kubernetes container security is no longer optional; it is fundamental to protecting infrastructure, data, and application integrity.
Understanding Docker & Kubernetes container security
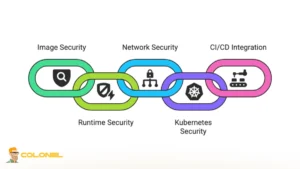
Docker & Kubernetes container security is a multi-layered security strategy that spans image creation, orchestration configuration, and runtime protection in production environments. When you implement it correctly, you protect three interconnected domains:
- The container image supply chain
- The Kubernetes control plane and workloads
- The runtime execution layer
Weakness in one area directly affects the others. A vulnerable Docker image deployed into a misconfigured Kubernetes cluster creates exponential risk exposure. Docker & Kubernetes container security ensures that both layers are hardened and continuously monitored to prevent lateral movement, privilege escalation, and data exfiltration.

The Container Security Landscape in Modern Cloud Environments
Container security operates within a dynamic cloud-native ecosystem where applications are decomposed into microservices and deployed rapidly. This velocity introduces agility but also expands the attack surface dramatically.
Containers share host kernels, rely on layered images, and depend on third-party packages. Kubernetes clusters expose APIs, manage service accounts, and control networking policies. Each of these elements introduces security considerations that require deliberate configuration and ongoing validation. As Mohammad-Ali A’râbi explains in ReasearchGate:

WordPress Web Hosting
Starting From $3.99/Monthly
“Container security resembles securing a building: strong entry points, intelligent access control, and constant surveillance are all required.”
This analogy highlights why Docker & Kubernetes container security must address build-time integrity, orchestration governance, and runtime visibility simultaneously.
Docker Container Security Fundamentals
Docker container security focuses primarily on image integrity, configuration discipline, and daemon hardening. Every deployed container inherits its blueprint from the image. A single flawed image can replicate vulnerabilities across dozens or hundreds of running instances.
These areas collectively determine whether your containerized application begins life in a secure state.

Securing Base Images and Dependencies
Docker & Kubernetes container security requires strict control over base images and application dependencies because they represent the most common entry points for vulnerabilities. Every Docker image starts from a base layer such as Ubuntu, Alpine, or Node, and these layers often contain known CVEs.

Cheap VPS Server
Starting From $2.99/Monthly
Using the :latest tag introduces unpredictability. It may pull in untested changes or newly disclosed vulnerabilities without warning. Instead, you should pin images to explicit versions such as node:18.17.1-alpine to maintain deterministic builds and controlled updates.
Open-source dependencies introduce additional exposure. Package managers like npm, pip, and Maven frequently incorporate third-party libraries that may contain exploitable flaws. Continuous container security scanning is essential to detect and remediate these issues before deployment.
Preventing Dockerfile Misconfigurations
Docker & Kubernetes container security also depends heavily on disciplined Dockerfile design. Seemingly minor configuration mistakes can produce significant security weaknesses. Always consider:
| Misconfiguration | Description | Mitigation |
| Running containers as root | Docker containers run with root by default. If compromised, attackers can gain host-level access. | Create and switch to a non-root user using the USER directive. |
| Hardcoding secrets | Embedding API keys, database credentials, or tokens in images exposes them permanently. | Use secret management systems or inject secrets via environment variables at runtime. |
| Excessive kernel capabilities | Containers with unnecessary kernel capabilities violate least privilege and increase risk if compromised. | Drop unneeded capabilities and restrict privilege escalation explicitly. |
Securing the Docker Daemon
The Docker daemon itself is a high-value target within Docker & Kubernetes container security. If exposed or misconfigured, it can grant attackers full control over the host system.
Mounting the Docker socket inside containers creates a severe risk because it effectively provides root-level control of the host environment. This practice should be avoided unless absolutely necessary and protected with strict access controls. Essential controls for maintaining daemon integrity include:
- Proper TLS configuration
- Restricted API exposure
- Minimized administrative access
Kubernetes Container Security Best Practices
Kubernetes introduces powerful automation capabilities but also increases complexity, which can amplify configuration errors.

Windows VPS Hosting
Remote Access & Full Admin
Kubernetes container security focuses on identity management, workload isolation, and pod-level restrictions.

Role-Based Access Control and Authentication
Docker & Kubernetes container security requires granular control over who can access cluster resources and what actions they can perform. Role-Based Access Control must always be enabled to define explicit permissions for users and service accounts.
Following the principle of least privilege ensures that identities receive only the permissions required for their operational responsibilities. Over-permissioned accounts represent a significant attack vector.
Strong authentication mechanisms such as OIDC or SAML integration with trusted identity providers, enhance cluster security posture. Static token files and weak authentication schemes increase exposure and should be avoided.
Namespace and Network Isolation
By default, Kubernetes networking allows unrestricted pod-to-pod communication within a cluster. Docker & Kubernetes container security must therefore enforce isolation through namespaces and network policies.
Namespaces create logical segmentation between applications, environments, or teams. They reduce the likelihood of unintended cross-application interference.
Network policies act as firewalls at the pod level. A default-deny configuration, where traffic is blocked unless explicitly permitted, establishes a robust security baseline. This approach minimizes lateral movement opportunities in case of compromise.
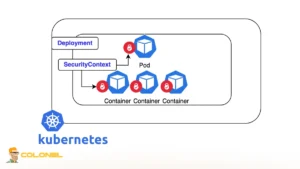
Pod Security Context and Container Controls
Pod security contexts provide granular configuration capabilities within Docker & Kubernetes container security frameworks. These settings determine user IDs, group IDs, and privilege parameters at both pod and container levels.
You should enforce non-root execution using runAsUser directives and disable privilege escalation by setting allowPrivilegeEscalation to false. Additionally, unnecessary capabilities must be dropped to align with least-privilege principles.
Managing these configurations across large clusters can become operationally challenging. Cloud Security Posture Management platforms can automate scanning and highlight deviations from best practices.
Container Security Scanning and Vulnerability Management
Security is not static; new CVEs emerge daily, and previously secure images can become vulnerable over time. Container security scanning integrates into CI/CD pipelines to detect vulnerabilities before images reach production. This “shift-left” approach reduces remediation cost and prevents vulnerable deployments.
Registry scanning ensures that images stored in repositories such as AWS ECR, Docker Hub, or GCR are monitored continuously. When new vulnerabilities are disclosed, scanning tools can alert teams even if images were previously considered safe.
For an updated overview of emerging tools, you may consult analyses such as Top Container Scanning Tools in 2025, which evaluates modern scanning capabilities and contextual prioritization features.
As highlighted in industry discussions, contextual prioritization is increasingly critical. Tools must determine whether a vulnerability is actually exploitable within your runtime context rather than relying solely on severity scores.
The Role of Runtime Container Security
Runtime container security focuses on detecting abnormal behavior in live containers. It monitors system calls, network activity, and file modifications to identify suspicious patterns.
This layer functions as real-time surveillance for your containerized environment. Without runtime visibility, organizations lack the ability to respond effectively to evolving threats. Effective runtime security solutions provide:
- Broad language and OS support: The tool must scan across all programming languages and base operating systems in your stack, ensuring comprehensive visibility rather than partial coverage.
- CI/CD integration: Seamless integration into GitHub Actions, GitLab pipelines, or other CI workflows ensures vulnerabilities are caught before code merges into production branches.
- Registry scanning: Continuous monitoring of container registries ensures new vulnerabilities are flagged even after images are built.
- Contextual prioritization: Advanced tools assess exploitability within your environment, reducing noise and improving remediation efficiency.
- Misconfiguration detection: Beyond CVEs, scanners should detect security misconfigurations such as root execution, excessive privileges, or embedded secrets.
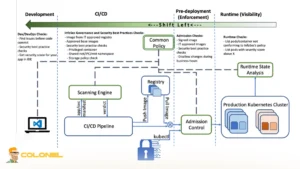
Step-by-Step Framework for Implementing Docker & Kubernetes Container Security
To establish a mature Docker & Kubernetes container security strategy, you should address the following phases in sequence, ensuring each layer reinforces the next.
- Secure the Image Build Process
You begin by hardening your Dockerfiles, pinning base image versions, eliminating unnecessary packages, and enforcing non-root execution. Automated container security scanning must be integrated into CI/CD pipelines to detect vulnerabilities before artifacts reach registries. - Harden the Container Registry
Your registry must enforce access control policies, vulnerability monitoring, and immutability standards. Registry scanning ensures newly disclosed CVEs are detected even after image publication. This stage strengthens supply chain integrity. - Enforce Kubernetes Access Controls
You should configure Role-Based Access Control with least-privilege policies for users and service accounts. Integrating Kubernetes authentication with enterprise identity providers reduces reliance on static tokens and enhances traceability. - Apply Network Segmentation and Isolation
Implement namespaces to separate environments and define strict network policies to prevent unrestricted pod communication. A default-deny approach ensures that only explicitly allowed traffic flows between workloads. - Enable Runtime Monitoring and Incident Response
Runtime container security tools monitor behavioral anomalies such as privilege escalation attempts or unexpected outbound network connections. Real-time alerting and forensic logging capabilities improve detection and containment.
This layered methodology ensures Docker & Kubernetes container security is not limited to build-time scanning but evolves into a continuous protection lifecycle.
Real-World Lessons from Container Security Incidents
Docker & Kubernetes container security best practices are often shaped by high-profile incidents that reveal systemic weaknesses.
The 2020 Tesla Kubernetes breach demonstrated how exposed Kubernetes dashboards without authentication can allow attackers to deploy cryptomining workloads. This incident underscores the importance of strong authentication and cluster access restrictions. As the Kubernetes documentation emphasizes:
“RBAC is an effective mechanism for controlling access to resources.”
This reinforces the central role of identity governance in container security.
Strategic Roadmap for Long-Term Container Security Maturity
Docker & Kubernetes container security evolves as organizational maturity increases. A phased roadmap helps align security improvements with operational capacity.
- Phase One focuses on foundational hygiene: image scanning, RBAC enforcement, and namespace isolation.
- Phase Two integrates automated policy enforcement, CI/CD pipeline scanning, and registry monitoring.
- Phase Three introduces advanced runtime monitoring, contextual prioritization, and continuous posture management.
By progressing incrementally, organizations reduce risk exposure while maintaining development agility.
Final Thoughts on Securing Modern Containerized Environments
Docker & Kubernetes container security is not a single configuration task but an ongoing operational discipline that integrates secure development, controlled orchestration, and continuous runtime monitoring. When these layers operate together, they create a resilient defense model capable of adapting to emerging threats.
Organizations that treat container security as a lifecycle responsibility rather than a compliance checkbox significantly reduce breach probability. By combining hardened images, controlled cluster governance, and runtime visibility, you establish a mature security posture aligned with modern cloud-native architectures.
Frequently Asked Questions About Docker & Kubernetes Container Security
What is Docker & Kubernetes container security?
Docker & Kubernetes container security refers to the comprehensive protection of container images, orchestration layers, and runtime environments to prevent vulnerabilities, misconfigurations, and active threats.
Why is runtime security necessary if images are scanned?
Runtime security detects zero-day vulnerabilities and behavioral anomalies that static scanning cannot identify before deployment.
How does RBAC improve Kubernetes security?
RBAC enforces least-privilege access control, limiting what users and service accounts can perform within the cluster.
What is the biggest risk in Docker container security?
Running containers as root and embedding secrets in images remain among the most critical and common security failures.
How often should container images be scanned?
Container images should be scanned continuously during CI/CD and periodically in registries to detect newly disclosed vulnerabilities.
