
A critical security flaw in the GNU InetUtils telnetd server (CVE-2026-24061) is being actively exploited by attackers worldwide. The telnetd vulnerability allows unauthenticated attackers to bypass standard login procedures and gain root access on affected Linux systems. Researchers have observed coordinated campaigns targeting the Telnet service, highlighting the severe risk posed to networked Linux infrastructure. Immediate patching and monitoring are essential to prevent compromise.
Understanding the telnetd Vulnerability (CVE-2026-24061)
The telnetd vulnerability resides in how the Telnet daemon passes the USER environment variable to the /usr/bin/login binary. By exploiting this flaw, attackers can bypass authentication entirely, allowing remote code execution with root privileges. The affected versions range from GNU InetUtils 1.9.3 through 2.7.
This vulnerability exploits a command injection scenario: when the Telnet daemon executes the login program, an attacker can manipulate the USER variable with the -f root flag. This tricks the system into treating the session as already authenticated, granting full administrative access without credentials.
“Active exploitation of a critical authentication bypass vulnerability in the GNU InetUtils telnetd server (CVE‑2026‑24061) has been observed in the wild, allowing unauthenticated attackers to gain root access to Linux systems.”_Guru Baran, CyberSecurityNews
Exploitation Flow and Attack Patterns
Attackers initiate connections to vulnerable Telnet servers (TCP/23) and deliver a crafted ENVIRON variable to exploit the authentication bypass. Once the telnetd vulnerability is executed, the payload immediately provides a root shell, enabling attackers to perform reconnaissance, deploy malware, or establish persistent access.

WordPress Web Hosting
Starting From $3.99/Monthly
The sophistication of these attacks is evident in the diversity of payload configurations, which include terminal speed, terminal type, and target usernames. These variations help attackers evade simple signature-based detection systems and automate large-scale compromise campaigns.
Observed Exploitation Campaigns
Recent honeypot analysis revealed multiple coordinated exploitation attempts. Attackers ranged from opportunistic scanners to more targeted campaigns aiming for long-term persistence on compromised systems. The observed behaviors indicate the potential formation of a botnet and large-scale reconnaissance across Linux servers. Notable attacker behaviors include:
- Immediate reconnaissance commands post-compromise (
uname -a,id,cat /etc/passwd). - SSH key injection for persistent access.
- Download and execution of second-stage Python payloads.
Indicators of Compromise (IOCs)
Below is a detailed table of observed attacker infrastructure and payloads associated with the telnetd vulnerability:
| Indicator Type | Value | Context |
| Attacker IP | 178.16.53[.]82 | Top source, multiple reconnaissance sessions |
| Attacker IP | 216.106.186[.]24 | SSH key injection and malware download |
| Attacker IP | 67.220.95[.]16 | Malware distribution and exploitation attempts |
| Attacker IP | 156.238.237[.]103 | Confirmed root access (IDS alert) |
| Malware URL | http://67.220.95[.]16:8000/apps.py | Second-stage Python payload |
| File Name | apps[.]py | Payload executed after initial compromise |
| SSH Key Comment | [email protected][.]hosting | Associated with persistent access attempts |
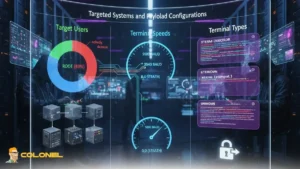
Targeted Systems and Payload Configurations
While root remains the primary target, opportunistic probes for other system accounts such as nobody, daemon, and randomized usernames have been observed. Telnetd vulnerability attackers employ variations in terminal speeds and terminal types to evade detection and ensure compatibility across diverse system environments.
These payload configurations allow the malicious session to blend with legitimate traffic and bypass basic signature-based security controls:
- Terminal Speeds: Commonly set to 9600 baud or 38400 baud, though some attacks negotiate 0,0 to evade detection in monitoring systems.
- Terminal Types: Sessions use XTERM-256COLOR, xterm-256color compatibility mode, or generic UNKNOWN types to maintain compatibility across multiple terminal emulators.
- Target Users: Root is the primary focus (approximately 83% of attacks), while other accounts, such as nobody, daemon, and random test users, are occasionally targeted for opportunistic compromise.

Cheap VPS Server
Starting From $2.99/Monthly
Persistence and Second-Stage Payloads
After successfully obtaining root access, telnetd vulnerability attackers frequently implement measures to maintain long-term control of compromised systems. Observed tactics include appending SSH keys to authorized user files and downloading additional payloads designed to automate reconnaissance, system modification, or botnet enrollment. These methods indicate a well-structured approach aimed at persistent access and potential lateral movement within the network.
- Persistence Strategy: SSH key injection to ensure seamless re-entry without requiring further authentication.
- Payload Deployment: Python-based scripts such as
apps.pyserve as second-stage payloads to automate system monitoring, data exfiltration, and preparation for additional malicious activities.
CVE and Severity
The telnetd vulnerability is classified as critical, reflecting its potential for total system compromise without authentication. All GNU InetUtils versions from 1.9.3 to 2.7 are affected, requiring urgent updates to mitigate exploitation risks.
| CVE ID | Severity | CVSS Score | Affected Versions |
| CVE-2026-24061 | Critical | 9.8 | GNU InetUtils 1.9.3 – 2.7 |
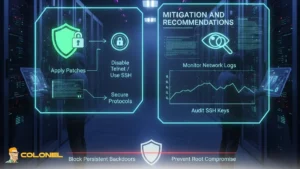
Mitigation and Recommendations
Organizations running Telnet services on Linux systems must take immediate action to prevent exploitation of CVE-2026-24061. Implementing layered defenses, applying patches, and auditing system access can significantly reduce risk. Administrators should follow these steps:
- Apply the latest GNU InetUtils updates to patch the telnetd vulnerability.
- Disable Telnet on public-facing servers wherever possible, replacing it with secure protocols such as SSH.
- Monitor network logs for unusual Telnet sessions, especially those attempting authentication bypass using
-f root. - Audit SSH authorized keys to remove any unauthorized entries added by attackers.
- Deploy intrusion detection systems capable of flagging abnormal environment variable injections and command sequences.
By following these recommendations, organizations can prevent root compromise, block persistent backdoors, and strengthen overall Linux server security. Also, you can visit Colonelserver SiteLock website security & malware protection service.
Strategic Implications
CVE-2026-24061 highlights a persistent threat to Linux infrastructures that continue to rely on legacy Telnet services. Attackers are capable of combining opportunistic exploitation with sophisticated payloads to achieve prolonged access, representing operational and strategic risks to enterprise servers, cloud environments, and hosting platforms.

Windows VPS Hosting
Remote Access & Full Admin
The telnetd vulnerability demonstrates that even older protocols, when left unpatched, can serve as entry points for critical breaches. This emphasizes the need for proactive system hardening and continuous monitoring across all Linux-based deployments.
