Het beschermen van uw website is de basis van geloofwaardigheid, en organische groei, en WordPress-beveiliging speelt een cruciale rol in hoe goed uw site bestand is tegen moderne cyberaanvallen. Wanneer uw platform veilig is, je voorkomt gegevensverlies, het vertrouwen van de klant beschermen, en de zichtbaarheid van zoekopdrachten behouden. In deze gids, u leert een professionele aanpak voor het beschermen van uw WordPress-omgeving met behulp van bewezen defensieve strategieën.
Waarom WordPress-beveiliging belangrijker is dan ooit
Het beveiligen van uw WordPress-site is essentieel omdat aanvallers voortdurend zoeken naar kwetsbare installaties, zwakke configuraties, of verouderde plug-ins die de deur openen voor uitbuiting. Een gecompromitteerde website kan gebruikers omleiden naar kwaadaardige pagina's, gevoelige informatie lekken, of zelfs helemaal uit de zoekresultaten worden verwijderd. Deze gevolgen zijn van invloed:
- merkreputatie
- operationele continuïteit
- SEO-stabiliteit op lange termijn
Effectieve WordPress-beveiligingsverdediging vereist meer dan een sterk wachtwoord; het hangt af van een meerlaagse architectuur met bescherming op serverniveau, verharding op toepassingsniveau, veilige codepraktijken, en voortdurende monitoring.

Veelvoorkomende oorzaken van WordPress-kwetsbaarheden
Begrijpen hoe aanvallers websites infiltreren is het startpunt van een robuuste verdedigingsstrategie. De meeste WordPress-beveiligingsfouten komen voort uit voorspelbare zwakheden, waardoor ze te voorkomen zijn met de juiste architectuur en operationele discipline.
Deze zwakke punten omvatten vaak verouderde componenten, slecht gecodeerde plug-ins, en zwakke authenticatiepraktijken, Deze kunnen allemaal worden uitgebuit door geautomatiseerde tools die het web scannen op gemakkelijke doelen.

WordPress -webhosting
Vanaf $ 3,99/maandelijks
Aanvallers kiezen zelden een specifiek slachtoffer; in plaats van, ze exploiteren sites die eenvoudigweg onbeschermd zijn. Dit betekent dat elke WordPress-installatie geen updates heeft, firewall-bescherming, of een goede toegangscontrole wordt een omgeving met een hoog risico.
De meest voorkomende toegangspunten
Voordat u uw verdedigingsstrategie verbetert, het is belangrijk om te begrijpen waar aanvallen doorgaans beginnen. Hier volgen de meest voorkomende vectoren die worden uitgebuit bij inbraken in de echte wereld:
- Gecompromitteerde wachtwoorden:
Zwakke of hergebruikte wachtwoorden blijven een belangrijke oorzaak van inbreuken, omdat geautomatiseerde bots duizenden combinaties per seconde kunnen testen. Zonder sterk, unieke referenties, inlogpagina's worden het gemakkelijkste pad naar een WordPress-installatie. - Kwetsbare plug-ins of thema's:
Verouderde componenten of nulled premium plug-ins bevatten vaak bekende kwetsbaarheden of verborgen achterdeurtjes. Zodra deze zijn geïnstalleerd, aanvallers kunnen de authenticatie omzeilen, code injecteren, of escaleer de rechten binnen uw systeem. - Slechte veiligheidshygiëne:
Onnodige gebruikersaccounts, buitensporige machtigingen, en niet-onderhouden installaties dragen allemaal bij aan een voorspelbare exploitatie. Wanneer het operationele beleid zwak is, aanvallers hebben veel minder verfijning nodig om uw omgeving in gevaar te brengen.
Een veilige hostingprovider kiezen
Uw hostingprovider fungeert als uw eerste technische beveiligingspartner, en uw WordPress-beveiligingsstrategie is sterk afhankelijk van de infrastructuur die uw site ondersteunt. Kolonel is veilig WordPress-hosting provider vermindert de blootstelling aan kwetsbaarheden op serverniveau, verzacht pogingen tot brute kracht, en biedt ingebouwde functies waarmee u snel kunt herstellen na incidenten.
Hoogwaardige WordPress-hosts bieden een op beveiliging gerichte architectuur, zoals geïsoleerde omgevingen, proactief patchen, realtime firewalls, en schaalbare toewijzing van middelen. Deze functies dragen bij aan betere prestaties, snellere reactie op incidenten, en minder mogelijkheden voor kwaadwillige activiteiten.
Waar u op moet letten in een veilige WordPress-host
Na evaluatie van talrijke hostingstandaarden, de volgende kenmerken weerspiegelen consequent een veilige en moderne omgeving:

Goedkope VPS -server
Vanaf $ 2,99/maandelijks
- Geautomatiseerde externe back-ups:
Back-ups die buiten de primaire serveromgeving zijn opgeslagen, verminderen het risico dat u uw volledige systeem kwijtraakt na een inbreuk of hardwarefout. - SSL-certificaten inbegrepen:
Gecodeerd verkeer beschermt gebruikersgegevens, voorkomt het onderscheppen van inloggegevens, en verbetert de geloofwaardigheid voor zowel klanten als zoekmachines. - Firewall- en malwarescannen:
Een ingebouwde firewall in combinatie met scannen van bestandssystemen helpt bij het identificeren en blokkeren van bedreigingen voordat ze escaleren naar diepere systeemlagen. - 24/7 Technische hulp:
Snelle responsteams versnellen de hersteltijd en begeleiden u bij de noodzakelijke herstelstappen na een incident. - Sterke reputatie en sectorrecensies:
Geverifieerde gebruikersfeedback en professionele evaluaties helpen bepalen of de provider consistent veilige en stabiele hosting levert.
Geavanceerde WordPress-beveiligingsmaatregelen
Om uw website echt te beschermen tegen geavanceerde aanvallen, u moet geavanceerde beveiligingsmaatregelen implementeren die elke laag van uw site bewaken en beschermen. Deze maatregelen zijn van cruciaal belang voor websites die gevoelige gegevens verwerken, e-commercetransacties, of hoge verkeersvolumes.
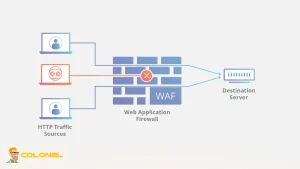
Implementeer een webapplicatie-firewall (WAF)
Een WordPress-firewall fungeert als schild, het filteren van binnenkomend verkeer om te voorkomen dat kwaadaardige verzoeken uw server bereiken. In tegenstelling tot generieke firewalls op serverniveau, een WAF is specifiek afgestemd op WordPress-kwetsbaarheden, bescherming tegen SQL-injecties, XSS-aanvallen, en geautomatiseerde brute-force-pogingen.
- Realtime detectie van bedreigingen: Houdt verdachte activiteiten in de gaten en blokkeert aanvallers onmiddellijk.
- Verkeersfiltering: Voorkomt dat kwaadaardige bots uw site overweldigen.
- Aangepaste regels: Hiermee kunnen geavanceerde gebruikers beveiligingsregels definiëren die zijn afgestemd op de structuur van hun website.
Investeren in een robuuste WAF zorgt ervoor dat uw website continu wordt verdedigd, het verminderen van het risico op downtime en gegevensdiefstal.
Monitor siteactiviteit en gebruikersrollen
Het bijhouden van een gedetailleerd activiteitenlogboek is cruciaal voor het vroegtijdig opsporen van verdacht gedrag. Door veranderingen bij te houden, aanmeldingen, en plug-in-updates, u kunt snel ongeautoriseerde acties identificeren voordat deze escaleren tot grootschalige inbreuken.
- Activiteitenregistratie: Legt vast wie wijzigingen heeft aangebracht en wanneer, het verstrekken van een forensisch spoor.
- Beheer van gebruikersrollen: Beperk de toegang op basis van verantwoordelijkheid: beheerders, redacteuren, en bijdragers mogen alleen toegang krijgen tot wat ze echt nodig hebben.
- Waarschuwingen en meldingen: Directe e-mail- of dashboardmeldingen wanneer er kritieke wijzigingen plaatsvinden.
Goede monitoring en beheer van gebruikersrollen helpen interne bedreigingen en onbedoelde verkeerde configuraties te voorkomen, die vaak over het hoofd worden gezien in basisbeveiligingsinstellingen.

Windows VPS-hosting
Remote Access & Full Admin
Regelmatige beveiligingsaudits
Zelfs met sterke plug-ins en firewallbescherming, uw website moet routinematige beveiligingsaudits ondergaan. Deze audits brengen kwetsbaarheden aan het licht, verouderde componenten, en misconfiguraties die geautomatiseerde systemen mogelijk missen.
- Plugin- en themarecensies: Zorg ervoor dat alle componenten up-to-date zijn en afkomstig zijn van vertrouwde bronnen.
- Controles van de bestandsintegriteit: Detecteert ongeautoriseerde wijzigingen aan kernbestanden.
- Scannen op kwetsbaarheden: Identificeert potentiële gaten in de beveiliging voordat hackers deze misbruiken.
Regelmatige audits fungeren als een preventieve maatregel, waardoor u inzicht krijgt in potentiële risico's en tijdige corrigerende maatregelen mogelijk maakt.
Een veilige WordPress-site herstellen en onderhouden
Zelfs een goed beveiligde website kan in gevaar komen als het onderhoud wordt verwaarloosd. In dit deel wordt de nadruk gelegd op herstelstrategieën, back-ups, en het handhaven van voortdurende bescherming.
Off-site en realtime back-ups instellen
Back-ups zijn uw laatste verdedigingslinie als er een inbreuk plaatsvindt. Door kopieën off-site en in realtime te bewaren, u minimaliseert gegevensverlies en downtime.
- Cloudopslag: Bewaar back-ups extern om herstel van de site te garanderen, zelfs als de server is aangetast.
- Realtime back-ups: Leg elke verandering vast, inclusief berichten, pagina's, en verkooptransacties.
- Gemakkelijke restauratie: Betrouwbare plug-ins zoals Jetpack Backup maken herstel met één klik mogelijk, het verminderen van de technische complexiteit.
Een back-upstrategie waarborgt de bedrijfscontinuïteit, vooral voor e-commerce winkels of websites met frequente updates.
Implementeer tweefactorauthenticatie (2FA)
Tweefactorauthenticatie voegt een extra beveiligingslaag toe aan uw WordPress-inloggegevens. Zelfs als een wachtwoord is gecompromitteerd, hackers hebben zonder de tweede verificatiefactor geen toegang tot de site.
- Beheerdersaccounts: Pas 2FA toe op alle gebruikers op beheerdersniveau voor maximale bescherming.
- Toegang van derden: Vereis tijdelijke 2FA-referenties voor ontwikkelaars of marketingteams.
- Integratie van plug-ins: De meeste premium beveiligingsplug-ins bevatten 2FA-installatie voor eenvoudige implementatie.
2FA vermindert het risico op ongeautoriseerde toegang aanzienlijk en versterkt de algehele WordPress-beveiliging.

Reactieplan voor gehackte sites
Zelfs met voorzorgsmaatregelen, er kan nog steeds sprake zijn van een inbreuk. Het hebben van een gedefinieerd responsplan zorgt voor een snel herstel en minimaliseert de schade.
- Identificeer de inbreuk: Gebruik activiteitenlogboeken en malwarescans om de omvang van de inbreuk te detecteren.
- Isoleer de getroffen gebieden: Schakel gecompromitteerde plug-ins of gebruikersaccounts tijdelijk uit.
- Herstellen vanaf back-up: Herstel snel naar een schone versie van uw site.
- Beveiliging bijwerken: Wachtwoorden wijzigen, verwijder verdachte gebruikers, en pas alle updates toe.
- Professionele hulp: Overweeg om beveiligingsexperts in te huren als de inbreuk ernstig is.
Een duidelijk responsplan vermindert de downtime, behoudt de reputatie, en beschermt bezoekersgegevens.
Langdurig WordPress-beveiligingsonderhoud
Het onderhouden van WordPress-beveiliging is een voortdurende verantwoordelijkheid. Zelfs na het implementeren van geavanceerde beschermingsmaatregelen, continue monitoring en proactieve updates zijn essentieel. Een veilige site voorkomt niet alleen aanvallen, maar behoudt ook de SEO-ranglijst, Gebruikersvertrouwen, en operationele stabiliteit.
Continu plug-in- en themabeheer
Verouderde of ongebruikte plug-ins en thema's zijn frequente toegangspunten voor hackers. Door uw WordPress-omgeving regelmatig te herzien, minimaliseert u kwetsbaarheden.
- Verwijder ongebruikte componenten: Ongebruikte plug-ins of extra thema's moeten worden verwijderd om de aanvalsoppervlakken te verkleinen.
- Update regelmatig: Update regelmatig alle actieve plug-ins en thema's, prioriteit geven aan degenen die beveiligingspatches ontvangen.
- Bronnen van plug-ins controleren: Gebruik alleen plug-ins en thema's van gerenommeerde ontwikkelaars om backdoors in nulled- of gratis versies te vermijden.
Door een gestroomlijnde en bijgewerkte omgeving te behouden, u verkleint de kans op op exploits gebaseerde inbreuken aanzienlijk. Volgens Jetpack:
“Een beveiligingsplug-in biedt u bescherming zonder dat u complexe serverinstellingen hoeft te beheren. Het scant op malware, blokkeert slecht verkeer, bewaakt uw sitebestanden, en waarschuwt u als er iets verandert.”

Voortdurend scannen op malware en bedreigingen
Zelfs een goed beveiligde site kan het doelwit zijn van geavanceerde malware of zero-day-kwetsbaarheden. Geautomatiseerde scantools helpen problemen vroegtijdig op te sporen, waardoor een snelle verzachting mogelijk is.
- Geplande scans: Voer regelmatig scans uit op malware, verdachte code, en potentiële kwetsbaarheden.
- Realtime monitoring: Waarschuwt beheerders onmiddellijk als er kwaadaardige activiteit wordt gedetecteerd.
- Geautomatiseerde oplossingen: Veel beveiligingsplug-ins kunnen veelvoorkomende bedreigingen oplossen zonder handmatige tussenkomst.
Proactief scannen zorgt ervoor dat bedreigingen worden aangepakt voordat ze escaleren tot schadelijke inbreuken.
Veilige gebruikers- en beheerderspraktijken
Menselijke fouten zijn vaak de zwakste schakel in de beveiliging van WordPress. Een krachtig beleid voor gebruikers en beheerders is essentieel voor de veiligheid op de lange termijn.
- Beperk de toegang: Geef alleen beheerdersrechten aan vertrouwde gebruikers.
- Dwing sterke wachtwoorden af: Vereist complex, unieke wachtwoorden en periodieke updates.
- Gebruikers opleiden: Train teamleden op het gebied van phishing-aanvallen, malware-bewustzijn, en veilige inlogpraktijken.
Een combinatie van technische controles en goed opgeleide gebruikers creëert een holistische verdediging tegen mogelijke aanvallen.
Planning voor rampenherstel
Zelfs met robuuste beveiliging, incidenten kunnen plaatsvinden. Een noodherstelplan zorgt ervoor dat uw WordPress-site snel kan herstellen van een inbreuk of storing.
- Back-upverificatie: Test back-ups regelmatig om er zeker van te zijn dat ze compleet en herstelbaar zijn.
- Noodprotocollen: Definieer stappen voor het isoleren en herstellen van aangetaste componenten.
- Communicatieplan: Informeer belanghebbenden en gebruikers op passende wijze bij het afhandelen van beveiligingsincidenten.
Het hebben van een duidelijk en getest noodherstelplan vermindert de downtime, beperkt de schade, en beschermt zowel uw gegevens als uw reputatie.
Regelmatige beveiligingsaudits en rapporten
Beveiliging op lange termijn is afhankelijk van consistente beoordeling. Door periodieke audits uit te voeren, kunt u uw beveiligingsmaatregelen verfijnen en u aanpassen aan nieuwe bedreigingen.
- Beveiligingsaudits: Controleer de bestandsrechten, integriteit van de plug-in, en serverinstellingen.
- Analyse van activiteitenlogboeken: Volg afwijkingen in gebruikersactiviteit om potentiële inbreuken te detecteren.
- Rapportage: Genereer periodieke rapporten zodat beheerders weloverwogen beveiligingsbeslissingen kunnen nemen.
Audits bieden een routekaart voor verbetering en helpen ervoor te zorgen dat de WordPress-beveiliging in de loop van de tijd robuust blijft.

Versterk vandaag nog uw WordPress-beveiliging
Het beveiligen van uw WordPress-site is geen eenmalige taak, maar een voortdurende inspanning die waakzaamheid en proactieve maatregelen vereist. Van het kiezen van een betrouwbare hostingprovider tot het implementeren van sterke wachtwoorden, tweefactorauthenticatie, en regelmatige back-ups, elke stap draagt bij aan een versterkte website.
Het negeren van WordPress-beveiligingsrisico’s kan ernstige gevolgen hebben, inclusief gederfde inkomsten, beschadigde reputatie, de stoelgegevens, en SEO-boetes. Door deze best practices te volgen en gebruik te maken van vertrouwde beveiligingstools, u kunt uw website beveiligen, het vertrouwen van de gebruiker behouden, en zorg voor een ononderbroken online aanwezigheid.
Veelgestelde vragen (FAQ) Over WordPress-beveiliging
Wat is de meest voorkomende manier waarop WordPress-sites worden gehackt??
De meest voorkomende toegangspunten zijn verouderde WordPress-kernbestanden, plug-ins, en thema's. Zwakke wachtwoorden, hergebruikte gebruikersnamen zoals “admin,En een slechte hostingbeveiliging vergroot het risico nog verder.
Heb ik een WordPress-beveiligingsplug-in nodig??
Ja. Beveiligingsplug-ins bieden continue bescherming door te scannen op malware, het monitoren van activiteit op de locatie, en het blokkeren van kwaadaardig verkeer.
Welke invloed heeft WordPress-beveiliging op de SEO- en Google-ranglijst??
Een gehackte site kan de SEO-ranglijst schaden door middel van zwarte lijsten, injectie van spam-inhoud, trage pagina laadt, en verlies van vertrouwen van de gebruiker. Google geeft de voorkeur aan beveiligde sites (HTTPS) en kan sites die zijn aangetast door malware of spam bestraffen of verwijderen.
Is tweefactorauthenticatie (2FA) noodzakelijk voor WordPress-beveiliging?
Absoluut. 2FA voegt een extra beschermingslaag toe door een tweede verificatiestap te vereisen, waardoor ongeautoriseerde toegang uiterst moeilijk wordt, zelfs als wachtwoorden worden gestolen.
Hoe kan ik detecteren of mijn WordPress-site is gehackt??
Borden bevatten veiligheidswaarschuwingen, ongebruikelijke omleidingen, malwarewaarschuwingen van plug-ins, verdachte regels code, onverwachte trage prestaties, en plotselinge stilstand.
